Crook Arrested For Millions In Office365 Executive Account Breaches
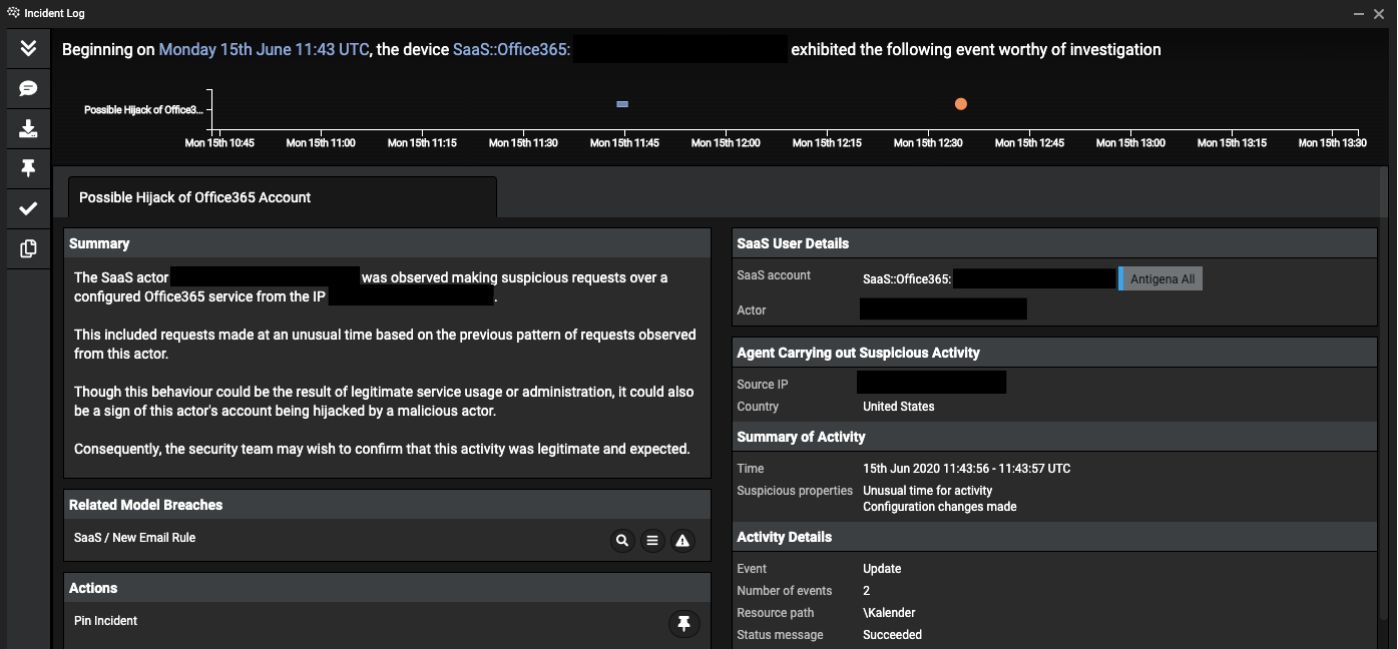
Table of Contents
The Modus Operandi: How the Breaches Occurred
This sophisticated cyberattack targeted high-value executive accounts, leveraging several common yet highly effective techniques. The criminal likely employed a multi-pronged approach, combining various methods to bypass security measures. Understanding these methods is crucial to preventing future Office365 security breaches.
-
Phishing and Social Engineering: Sophisticated phishing campaigns, mimicking legitimate communications from trusted sources, were likely used to trick executives into revealing their login credentials. These emails often contained malicious links or attachments designed to install malware or steal information. The attacker likely leveraged social engineering tactics to increase the likelihood of successful phishing attempts.
-
Credential Stuffing and Exploiting Vulnerabilities: The attacker may have used credential stuffing – trying previously compromised usernames and passwords obtained from other data breaches – to access accounts. They may have also exploited known vulnerabilities in Office365, using publicly available exploits or zero-day vulnerabilities to gain unauthorized access.
-
The Failure of Multi-Factor Authentication (MFA): A significant contributing factor was likely the lack of, or failure to implement, multi-factor authentication (MFA). MFA adds an extra layer of security, requiring users to provide a second form of verification beyond just a password. Without MFA, compromised credentials are far more easily exploited.
-
Bullet Points:
- Sophisticated phishing emails mimicking legitimate communications.
- Exploitation of weak passwords and reused credentials.
- Use of stolen credentials from other data breaches (credential stuffing).
- Lack of MFA enabled accounts, allowing single-factor authentication compromise.
The Financial and Reputational Damage
The financial and reputational impact of this Office365 security breach is substantial. The affected companies suffered significant losses across multiple areas.
-
Financial Losses: Millions of dollars were stolen directly from compromised accounts, impacting financial performance and potentially triggering significant financial instability. Beyond the direct theft, there are the costs associated with investigation, remediation, legal fees, and potential compensation to affected parties.
-
Reputational Damage: The breach severely damaged the reputation of the affected companies. Loss of customer trust, damage to brand image, and negative media coverage can have lasting consequences, impacting future business opportunities.
-
Legal Ramifications and Regulatory Fines: The organizations involved face potential lawsuits from affected parties, and may be subject to significant regulatory fines for failing to meet data protection and security standards. Compliance violations related to data privacy regulations (like GDPR or CCPA) are very likely.
-
Bullet Points:
- Millions of dollars in stolen funds.
- Damage to brand reputation and loss of customer trust.
- Potential lawsuits from affected parties and customers.
- Significant regulatory fines for non-compliance.
The Arrest and Legal Proceedings
Law enforcement agencies played a crucial role in investigating this major cybercrime and apprehending the perpetrator.
-
International Collaboration: The arrest involved international collaboration between law enforcement agencies, highlighting the global nature of cybercrime and the need for coordinated responses.
-
Criminal Charges: The individual faces serious criminal charges related to data theft, unauthorized access to computer systems, and financial fraud. The specific charges will vary depending on the jurisdiction.
-
Ongoing Legal Proceedings: The legal proceedings are ongoing, with the individual facing potential lengthy imprisonment and substantial fines. The severity of the sentencing will depend on several factors, including the scale of the crime and the extent of the damages.
-
Bullet Points:
- International collaboration between law enforcement agencies.
- Seizure of assets and digital evidence during the investigation.
- Charges filed under relevant cybersecurity laws and financial crime statutes.
- Potential lengthy prison sentence and significant fines.
Lessons Learned and Best Practices for Office365 Security
This Office365 security breach underscores the critical need for organizations to proactively implement robust security measures.
-
Security Awareness Training: Regular and comprehensive security awareness training for all employees is essential. This training should cover phishing identification, password security best practices, and the importance of reporting suspicious activity.
-
Multi-Factor Authentication (MFA): Implementing MFA for all Office365 accounts is non-negotiable. This significantly reduces the risk of unauthorized access even if credentials are compromised.
-
Password Management: Enforce strong password policies and encourage the use of password managers to improve password hygiene. Regular password changes and avoidance of password reuse are crucial.
-
Vulnerability Management: Regular security audits and vulnerability assessments are necessary to identify and address potential weaknesses in the Office365 environment. Prompt patching of identified vulnerabilities is critical.
-
Incident Response Plan: A well-defined incident response plan is crucial for handling security breaches effectively and minimizing damage. This plan should include clear procedures for detection, containment, eradication, recovery, and post-incident analysis.
-
Bullet Points:
- Mandatory multi-factor authentication (MFA) for all accounts.
- Regular security awareness training for employees to combat phishing.
- Strong password policies and the use of password managers.
- Regular security audits and vulnerability assessments to identify weaknesses.
- A well-defined incident response plan for effective breach management.
Conclusion
The arrest of the individual responsible for the massive Office365 executive account breaches serves as a stark reminder of the ever-present threat of sophisticated cyberattacks. The incident underscores the critical need for organizations to prioritize robust cybersecurity measures to protect their valuable data and reputation. This case highlights the devastating consequences of neglecting Office365 security best practices.
Call to Action: Don't become the next victim. Strengthen your Office365 security posture today by implementing best practices and investing in comprehensive cybersecurity solutions. Learn more about protecting your organization from Office365 security breaches and avoid becoming the next headline. Prioritize Office365 security and safeguard your valuable data.

Featured Posts
-
 Novela Zakona O Romski Skupnosti Kaj Prinasa Javna Obravnava
May 13, 2025
Novela Zakona O Romski Skupnosti Kaj Prinasa Javna Obravnava
May 13, 2025 -
 The Downside Of Bollywood High Profile Flops And Departing Actresses
May 13, 2025
The Downside Of Bollywood High Profile Flops And Departing Actresses
May 13, 2025 -
 Large Scale Search For Missing Elderly Hiker In Peninsula Hills
May 13, 2025
Large Scale Search For Missing Elderly Hiker In Peninsula Hills
May 13, 2025 -
 Analyzing The Odds Will The Toronto Raptors Draft Cooper Flagg
May 13, 2025
Analyzing The Odds Will The Toronto Raptors Draft Cooper Flagg
May 13, 2025 -
 The Da Vinci Code Fact Vs Fiction In Dan Browns Bestseller
May 13, 2025
The Da Vinci Code Fact Vs Fiction In Dan Browns Bestseller
May 13, 2025
Latest Posts
-
 Aide Et Solidarite Accrues Pour Les Demandeurs D Asile A Bourg En Bresse
May 14, 2025
Aide Et Solidarite Accrues Pour Les Demandeurs D Asile A Bourg En Bresse
May 14, 2025 -
 Demandeurs D Asile A Bourg En Bresse Plus De Consideration Pour L Aide Et La Solidarite
May 14, 2025
Demandeurs D Asile A Bourg En Bresse Plus De Consideration Pour L Aide Et La Solidarite
May 14, 2025 -
 Violations De Droits Par Oqtf L Udr Appelle A L Indemnisation Des Victimes
May 14, 2025
Violations De Droits Par Oqtf L Udr Appelle A L Indemnisation Des Victimes
May 14, 2025 -
 Solidarite A Bourg En Bresse Une Situation Amelioree Pour Les Demandeurs D Asile
May 14, 2025
Solidarite A Bourg En Bresse Une Situation Amelioree Pour Les Demandeurs D Asile
May 14, 2025 -
 Oqtf L Udr Demande Une Indemnisation Immediate Pour Les Victimes De Violations Des Droits
May 14, 2025
Oqtf L Udr Demande Une Indemnisation Immediate Pour Les Victimes De Violations Des Droits
May 14, 2025
