Data Breaches Cost T-Mobile $16 Million: A Three-Year Security Lapse
Table of Contents
The Scale of the T-Mobile Data Breach
The T-Mobile data breach affected a massive number of customers, exposing sensitive personal information. While the exact figure fluctuates depending on the specific breach referenced (T-Mobile has experienced multiple breaches), millions of customer records were compromised. The types of data exposed were extensive, including:
- Personal Information: Names, addresses, dates of birth, Social Security numbers, and driver's license information.
- Financial Data: Account numbers, credit card details (in some cases), and banking information.
- Account Details: T-Mobile account numbers, usernames, passwords, and other login credentials.
The $16 million penalty represents only a portion of the overall cost. T-Mobile also incurred significant expenses related to:
- Legal Fees: Costs associated with investigations, lawsuits, and regulatory compliance.
- Customer Support: Handling customer inquiries, providing credit monitoring services, and addressing concerns.
- Remediation Costs: Expenses incurred in fixing the vulnerabilities and enhancing security systems.
The sheer scale of the data loss and the extensive financial repercussions underscore the critical importance of robust cybersecurity measures and effective data breach response plans. The keywords "customer data," "data loss," and "financial penalties" highlight the severity of the consequences.
Root Causes of the Three-Year Security Lapse
The T-Mobile data breach wasn't a result of a single, easily identifiable vulnerability. Instead, it stemmed from a combination of factors that allowed the breach to persist for three years:
- System Vulnerabilities: Weaknesses in T-Mobile's IT infrastructure allowed unauthorized access to sensitive customer data.
- Lack of Proactive Security Measures: Insufficient investment in proactive security measures, such as regular security audits and penetration testing, allowed vulnerabilities to remain undetected for an extended period.
- Inadequate Employee Training: A lack of comprehensive cybersecurity awareness training for employees contributed to the vulnerability.
- Outdated Technology: Using outdated or unsupported systems created exploitable weaknesses.
- Insufficient Cybersecurity Budgets: Limited resources allocated to cybersecurity initiatives hindered the company's ability to implement and maintain effective security measures.
These contributing factors, highlighted by keywords like "system vulnerabilities," "cybersecurity weaknesses," "lack of security measures," and "employee training," demonstrate a systemic failure in T-Mobile's security posture.
The Aftermath and Regulatory Response
Following the discovery of the breach, T-Mobile initiated several actions, including:
- Notification of Affected Customers: Informing customers about the breach and offering credit monitoring services.
- Investigation of the Breach: Conducting thorough internal and external investigations to identify the root causes.
- Implementation of Security Improvements: Investing in new technologies and security protocols to strengthen its defenses.
The breach also triggered regulatory investigations and penalties, including the aforementioned $16 million fine. Furthermore, class-action lawsuits were filed by affected customers, adding to the legal and financial burdens. Keywords like "regulatory response," "security improvements," "data breach investigation," and "legal ramifications" illustrate the far-reaching consequences.
Lessons Learned and Best Practices for Data Protection
The T-Mobile data breach provides valuable lessons for organizations of all sizes. Key takeaways include:
- Proactive Security Measures are Crucial: Regular security audits, penetration testing, and vulnerability assessments are essential for identifying and mitigating potential threats.
- Invest in Employee Training: Comprehensive cybersecurity awareness training for employees is crucial for preventing human error, a major factor in many breaches.
- Implement Robust Security Protocols: Multi-factor authentication, data encryption, and access control measures are vital for protecting sensitive data.
- Develop a Comprehensive Cybersecurity Strategy: A well-defined cybersecurity strategy that addresses all aspects of data protection is necessary.
By prioritizing data protection best practices, organizations can significantly reduce their risk of experiencing costly and damaging data breaches. The keywords "data protection best practices," "cybersecurity strategy," "preventing data breaches," "security audits," and "multi-factor authentication" summarize the essential steps organizations should take.
Conclusion: Avoiding Costly Data Breaches – Lessons from T-Mobile
The T-Mobile data breach serves as a cautionary tale, illustrating the significant financial and reputational damage that can result from inadequate data security. The three-year lapse underscores the importance of proactive security measures, robust cybersecurity strategies, and comprehensive employee training in preventing data breaches. The lessons learned from this incident should prompt all organizations to prioritize data security and implement best practices to avoid the costly consequences of a data breach. Invest in robust data security measures today to avoid the costly consequences of a data breach and safeguard your valuable customer information.

Featured Posts
-
 Unlock Cody Rhodes And The Undertaker Fortnite Skins A Complete Guide
May 03, 2025
Unlock Cody Rhodes And The Undertaker Fortnite Skins A Complete Guide
May 03, 2025 -
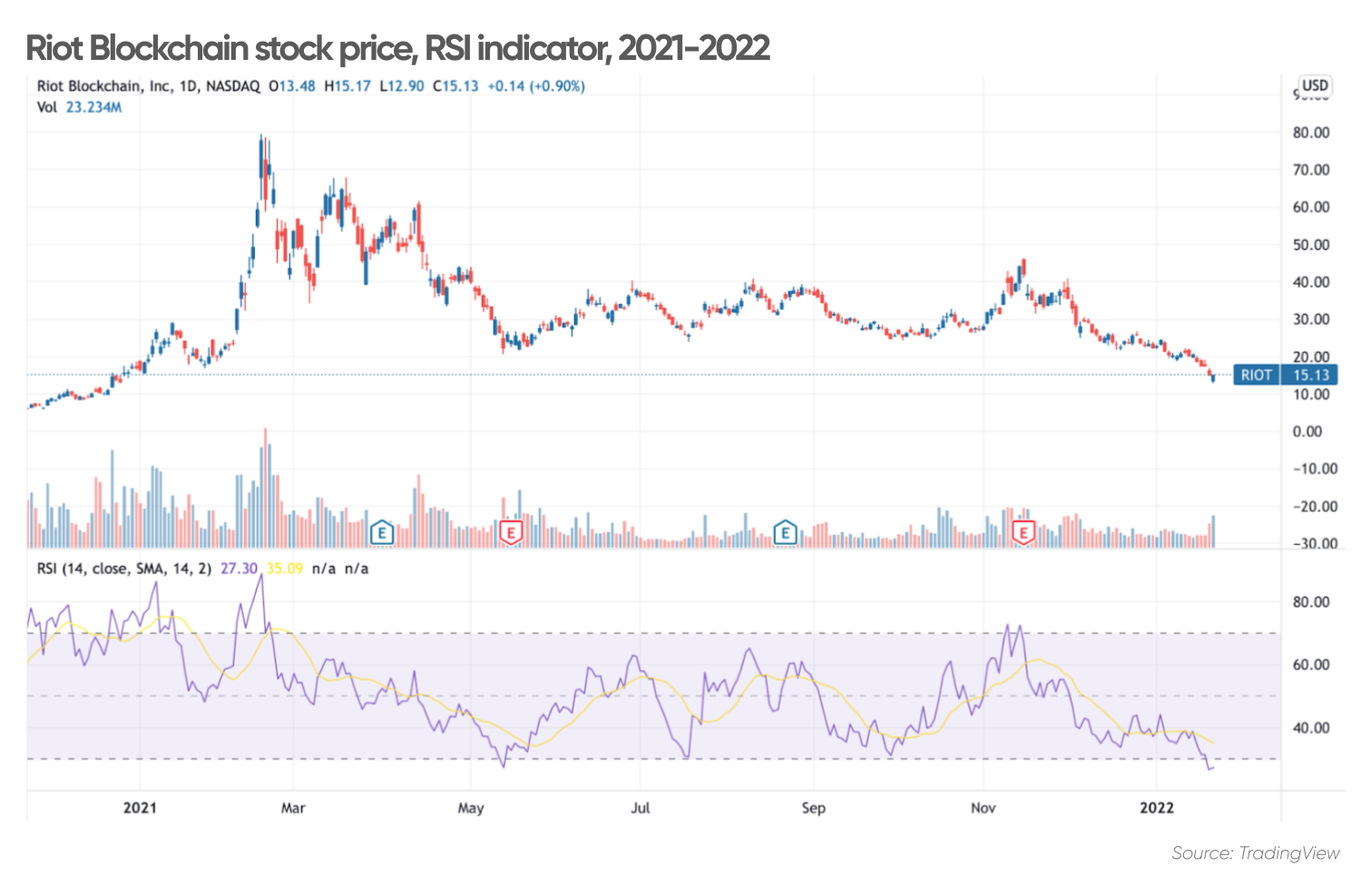 Understanding The Recent Decline In Riot Platforms Riot Stock Price
May 03, 2025
Understanding The Recent Decline In Riot Platforms Riot Stock Price
May 03, 2025 -
 Guido Fawkes Energy Policy Reform Shifts Direction
May 03, 2025
Guido Fawkes Energy Policy Reform Shifts Direction
May 03, 2025 -
 Poppys Family Issues Emotional Tribute Following Death Of Young Manchester United Supporter
May 03, 2025
Poppys Family Issues Emotional Tribute Following Death Of Young Manchester United Supporter
May 03, 2025 -
 Valorant Mobile Tencents Pubg Studio Developing A Mobile Version
May 03, 2025
Valorant Mobile Tencents Pubg Studio Developing A Mobile Version
May 03, 2025
