Deepfake Detection Foiled: Cybersecurity Expert's Clever Tactics
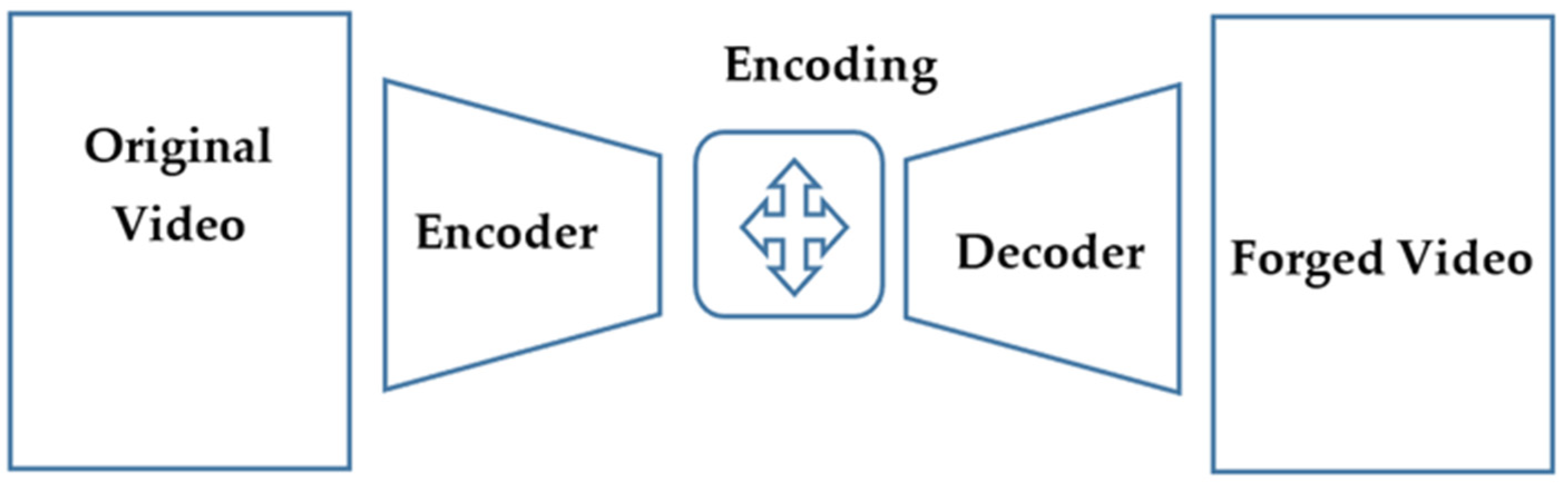
Table of Contents
The Expert's Methodology: Bypassing Current Deepfake Detection Techniques
Current deepfake detection technology relies heavily on AI algorithms. However, a cybersecurity expert has shown that these systems can be easily outmaneuvered with surprisingly simple techniques. This underscores the critical need for more sophisticated and adaptable deepfake detection strategies.
Exploiting Limitations in Current AI Detection Systems
Current deepfake detection primarily relies on analyzing subtle inconsistencies. These inconsistencies often manifest as unnatural blinking patterns, unrealistic facial expressions, or inconsistencies in lighting and shadowing. AI algorithms are trained to identify these visual cues. However, the expert demonstrated how easily these inconsistencies could be masked, rendering standard AI detection tools ineffective.
- Targeted manipulation of video compression artifacts: By carefully adjusting compression settings during the deepfake creation process, the expert was able to minimize or eliminate the telltale artifacts often used by AI to identify manipulated videos. This involved fine-tuning the encoding process to reduce the visual discrepancies.
- Introduction of subtle, imperceptible noise to disrupt analysis: Adding carefully calibrated noise to the deepfake video effectively disrupted the algorithms' ability to analyze the video's underlying structure. This noise was designed to be imperceptible to the human eye but significant enough to confuse the AI.
- Use of advanced deepfake software that inherently produces more realistic outputs: Newer deepfake software is constantly evolving, producing increasingly realistic results. The expert utilized the latest software, minimizing the visual inconsistencies exploited by current detection methods. This underscores the need for detection systems that can adapt to the constant improvements in deepfake technology.
Focusing on the "Unseen" Aspects of Deepfakes
The expert went beyond visible inconsistencies, focusing on metadata and other less-examined aspects of video files. While analyzing metadata (creation date, GPS data, camera model, etc.) is a powerful method for detecting deepfakes, this data can be easily manipulated or removed.
- Metadata manipulation and removal techniques: The expert demonstrated how simple it is to alter or completely erase metadata from video files. This makes it extremely difficult for investigators to trace the video's origin or detect signs of manipulation. This highlights the need for more robust methods of preserving and verifying video metadata.
- Exploiting weaknesses in forensic software capabilities: Many forensic software packages struggle to reliably identify deepfakes, especially those that have been carefully crafted to avoid detection. The expert exploited known weaknesses in these tools, rendering them ineffective.
- Use of steganography to hide additional data within the video file: The expert successfully embedded additional data within the video file using steganography – the art of hiding data within other data. This hidden data could be used to further obscure the deepfake's origin or to introduce additional layers of deception.
Implications for Cybersecurity and Fraud Prevention
The expert's success underscores the limitations of current deepfake detection technologies. This highlights the urgent need for a multi-layered approach, encompassing both technological advancements and a heightened awareness.
- The vulnerability of social media platforms to deepfake manipulation: Social media platforms, with their vast reach and relatively low barriers to entry, remain particularly vulnerable to deepfake manipulation. This can have severe consequences, impacting public opinion and potentially influencing elections.
- The potential for financial fraud using deepfake impersonations: Deepfakes are increasingly being used for financial fraud, such as impersonating executives to authorize fraudulent transactions. The implications are severe, potentially leading to significant financial losses for individuals and organizations.
- The legal and ethical challenges posed by sophisticated deepfakes: The legal and ethical ramifications of deepfakes are still largely unresolved. Determining accountability and establishing legal frameworks to address the misuse of deepfake technology remains a major challenge.
Future Directions in Deepfake Detection: The Need for Proactive Strategies
Future deepfake detection methods must adopt a more holistic approach, moving beyond simple visual analysis and integrating diverse techniques.
- Development of advanced AI models specifically designed to counter evolving deepfake techniques: Future AI models need to be designed with adaptability and resilience in mind, continuously learning and adapting to the evolving tactics used by deepfake creators.
- Integration of blockchain technology to verify video authenticity: Blockchain technology offers a potential solution for verifying the authenticity of videos. By creating a tamper-proof record of a video's creation and distribution, blockchain could help prevent the spread of deepfakes.
- Promotion of media literacy to help individuals identify potential deepfakes: Educating individuals on how to identify potential deepfakes is crucial. This involves developing critical thinking skills and promoting a healthy skepticism towards online content.
Conclusion
The cybersecurity expert's successful circumvention of existing deepfake detection methods serves as a stark reminder of the ongoing challenge posed by this technology. Current reliance on single-method detection is insufficient. A multi-faceted approach combining AI analysis, forensic investigation, and human review, along with proactive strategies like improved media literacy and technological advancements, is crucial for effective deepfake detection. We must stay vigilant and continually adapt our countermeasures to combat the ever-evolving threat of deepfakes. Learn more about protecting yourself and your organization from deepfake threats – explore advanced deepfake detection methods and best practices today.

Featured Posts
-
 Why Were These 10 Great Tv Shows Cancelled Unfinished Stories
May 17, 2025
Why Were These 10 Great Tv Shows Cancelled Unfinished Stories
May 17, 2025 -
 El Futuro De Los Prestamos Estudiantiles Bajo Una Segunda Administracion Trump
May 17, 2025
El Futuro De Los Prestamos Estudiantiles Bajo Una Segunda Administracion Trump
May 17, 2025 -
 Luxury Real Estate The Ultra Wealthys Strategy For Market Uncertainty
May 17, 2025
Luxury Real Estate The Ultra Wealthys Strategy For Market Uncertainty
May 17, 2025 -
 Analyzing The China Factor Challenges And Opportunities For Bmw Porsche And Similar Brands
May 17, 2025
Analyzing The China Factor Challenges And Opportunities For Bmw Porsche And Similar Brands
May 17, 2025 -
 Hardaway Jr Shot Controversy Crew Chief Admits To Missed Call
May 17, 2025
Hardaway Jr Shot Controversy Crew Chief Admits To Missed Call
May 17, 2025
