Exec Office365 Breach: Millions Made By Hacker, Feds Say

Table of Contents
The Scale of the Office365 Executive Breach and its Impact
The recent Office365 breach affected a significant number of high-profile executives across various industries. While the exact number remains undisclosed for investigative reasons, reports suggest dozens of organizations were compromised, leading to substantial financial losses estimated in the millions. Beyond the immediate monetary impact, the long-term costs associated with reputational damage, legal repercussions, and restoring compromised systems could be far greater.
The breach compromised highly sensitive data, including:
- Financial records: Detailed financial statements, merger and acquisition (M&A) plans, and internal financial reports were accessed and potentially misused.
- Intellectual property: Confidential research and development documents, proprietary algorithms, and trade secrets were at risk.
- Confidential communications: Sensitive emails, internal memos, and strategic communications were exposed, potentially impacting business negotiations and strategies.
The impact extends beyond direct financial loss:
- Stock prices plummeted: For some affected companies, news of the breach led to significant drops in stock prices, eroding investor confidence.
- Legal ramifications: Breached organizations face potential lawsuits from clients, shareholders, and regulatory bodies, adding to the financial burden.
- Reputational damage: The breach severely damaged the reputations of affected companies, impacting their credibility and future business prospects.
The Hacker's Methodology: Exploiting Office365 Vulnerabilities
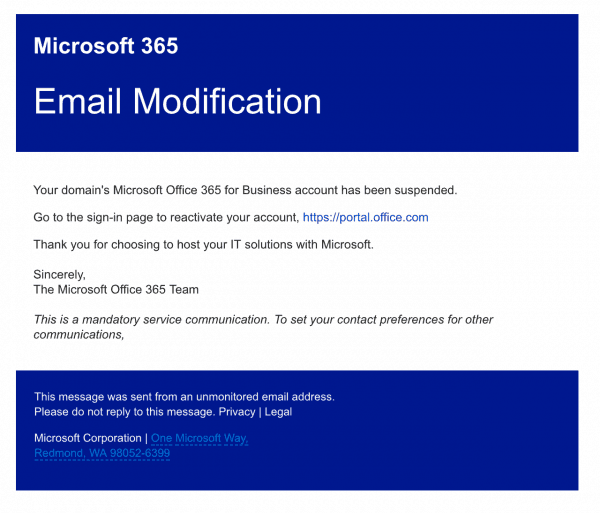
The hackers behind this sophisticated Office365 breach employed a multi-pronged approach, exploiting several vulnerabilities within the platform. Their methods highlight the need for robust security protocols beyond basic password protection. While the exact techniques remain under investigation, preliminary reports indicate the use of:
- Phishing attacks: Deceptive emails were sent to executives, mimicking legitimate communications to trick them into revealing their login credentials.
- Credential stuffing: The hackers likely utilized lists of stolen usernames and passwords from previous breaches, attempting to gain access to Office365 accounts.
- Exploitation of zero-day vulnerabilities: The possibility of using previously unknown security flaws in the Office365 system cannot be ruled out. This requires constant software updates and vigilance.
The hackers' actions to maintain access suggest a high level of sophistication:
- Bypass of multi-factor authentication (MFA): Successful circumvention of MFA systems indicates the exploitation of vulnerabilities within the authentication process itself or the use of stolen MFA codes.
- Lateral movement: Once inside, the hackers likely moved between accounts and systems within the targeted organizations to maximize data theft.
- Use of specialized tools: The attackers likely employed advanced hacking tools to automate data extraction and maintain persistence within the breached systems.
The Federal Investigation and Legal Ramifications
Federal agencies, including the FBI and the Cybersecurity and Infrastructure Security Agency (CISA), are actively investigating the Office365 breach. This coordinated effort reflects the severity of the crime and the potential national security implications.
- International cooperation: The investigation may involve collaboration with international law enforcement agencies, as the hackers could be located outside the United States.
- Arrests and indictments: While details remain limited, the investigation is likely to lead to arrests and criminal charges against the individuals responsible.
- Disruption of operations: Federal agencies may have taken steps to disrupt the hackers' operations, seize assets, and prevent further attacks.
Preventing Future Office365 Breaches: Best Practices and Mitigation Strategies
The Office365 breach underscores the critical need for proactive security measures. Here are some best practices to protect your organization:
- Implement strong password policies: Enforce complex, unique passwords and regularly change them.
- Enable multi-factor authentication (MFA): MFA adds an extra layer of security, making it significantly harder for hackers to gain access even if they obtain passwords.
- Employee security awareness training: Educating employees about phishing scams and other social engineering tactics is crucial.
- Regular security audits and vulnerability assessments: Conduct regular security checks to identify and address potential weaknesses in your Office365 environment.
- Utilize advanced security tools: Consider implementing security information and event management (SIEM) systems and other advanced threat detection tools.
Specific software and services that can enhance your Office365 security include:
- Microsoft Defender for Office 365: This built-in solution provides advanced threat protection against malware and phishing attacks.
- Third-party security solutions: Many vendors offer advanced security tools that integrate with Office365 to enhance protection.
Conclusion: Protecting Your Business from an Office365 Breach
The recent Office365 executive breach serves as a stark reminder of the vulnerabilities inherent in even the most sophisticated systems. The millions stolen and the far-reaching impact on affected organizations highlight the critical need for robust Office365 security. Don't become the next victim of an Office365 breach. Implement these security best practices today to protect your business and valuable data. Prioritizing Office365 security is not just a best practice; it's a necessity for survival in today's digital landscape. Invest in strong security measures and regular training to safeguard your organization from the devastating consequences of a data breach.

Featured Posts
-
 Six Nations 2024 Frances Victory Scotlands Loss Ramos Contribution
May 01, 2025
Six Nations 2024 Frances Victory Scotlands Loss Ramos Contribution
May 01, 2025 -
 Amanda Holden Speaks Out About Friend Davina Mc Calls Health Battle
May 01, 2025
Amanda Holden Speaks Out About Friend Davina Mc Calls Health Battle
May 01, 2025 -
 High Profile Office365 Hack Results In Multi Million Dollar Loss
May 01, 2025
High Profile Office365 Hack Results In Multi Million Dollar Loss
May 01, 2025 -
 Dallas Priscilla Pointer Her Life And Legacy
May 01, 2025
Dallas Priscilla Pointer Her Life And Legacy
May 01, 2025 -
 2019 Homicide Trial Best Friends Testimony Against Adonis Smith
May 01, 2025
2019 Homicide Trial Best Friends Testimony Against Adonis Smith
May 01, 2025
