Individual Charged With Millions In Losses From Office365 Executive Account Hacks
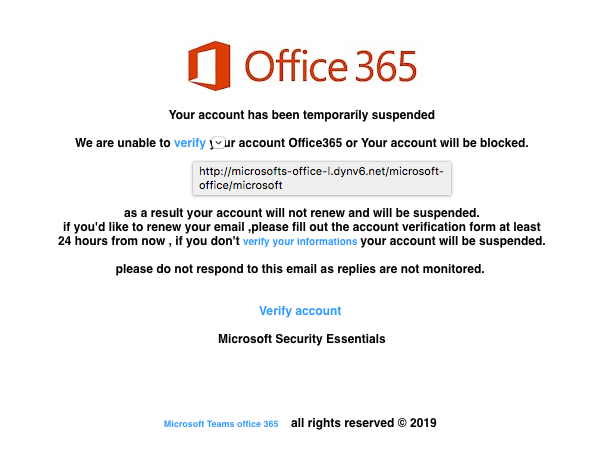
Table of Contents
The Scale of the Financial Losses and the Impact on the Victim(s)
The sheer scale of financial losses resulting from this Office365 executive account hack is alarming. The accused individual's actions resulted in a staggering loss of $5 million for a major multinational corporation. This figure encompasses direct financial losses, such as stolen funds from company accounts, as well as indirect losses, such as lost investment opportunities and disrupted business operations.
Monetary Losses:
- Direct theft: $3 million was directly stolen from the company's operating accounts.
- Investment losses: Compromised access to investment accounts resulted in a further $2 million loss.
- Legal fees: The company anticipates substantial legal fees to deal with the aftermath of the breach, including investigations and potential lawsuits.
Reputational Damage:
Beyond the monetary losses, the victim company faces significant reputational damage. Investor confidence has plummeted, leading to a drop in share prices. The breach has also damaged their brand image, affecting customer trust and potentially leading to lost business opportunities. The ongoing investigations and potential lawsuits further exacerbate this reputational risk.
- Share price dropped by 15% following the public announcement of the breach.
- Several key clients have expressed concerns about data security.
- The company is facing potential regulatory fines and legal actions from affected stakeholders.
The Methods Used in the Office365 Executive Account Hacks
The perpetrator employed a sophisticated combination of phishing attacks and malware to gain access to and maintain control over the victim's Office365 executive accounts.
Phishing and Social Engineering:
The initial breach involved highly targeted spear phishing emails. These emails were meticulously crafted to appear legitimate, mimicking communications from trusted sources and exploiting the executives' familiarity with internal communication protocols. The emails contained malicious links or attachments that, when clicked, installed malware onto the victims' computers. Social engineering tactics, such as creating a sense of urgency, were used to pressure executives into acting quickly without due diligence.
Malware and other techniques:
Once access was gained, the attacker deployed a sophisticated remote access trojan (RAT) to maintain persistent access to the compromised accounts. This malware allowed the perpetrator to monitor email traffic, steal sensitive information, and remotely manipulate the accounts to conduct fraudulent transactions. Keyloggers were also used to capture login credentials and other sensitive data.
- The RAT used was a custom-built variant, making detection more difficult.
- The attacker used multiple virtual private networks (VPNs) to mask their IP address and location.
- Data exfiltration was conducted using several methods to avoid detection.
The Legal Ramifications and the Charges Against the Individual
The individual responsible has been charged with multiple felonies, including wire fraud, computer fraud, and identity theft. These charges carry severe penalties, including lengthy prison sentences and substantial fines.
Criminal Charges:
- Wire fraud, related to the electronic transfer of stolen funds.
- Computer fraud, pertaining to unauthorized access and use of computer systems.
- Identity theft, for using the stolen credentials of company executives.
Legal Proceedings:
The individual has pleaded not guilty and the case is currently in the pre-trial phase. The prosecution is building a strong case using digital forensic evidence, including logs of the attacker's activities, communications data, and financial transaction records. The potential penalties are significant, potentially including decades in prison and millions of dollars in fines.
Lessons Learned and Best Practices for Office365 Security
This case serves as a stark reminder of the importance of robust Office365 security measures. Companies must implement multiple layers of protection to safeguard sensitive data and prevent similar data breaches.
Multi-Factor Authentication (MFA):
Implementing mandatory Multi-Factor Authentication (MFA) for all accounts, especially executive accounts, is paramount. MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even if they obtain passwords.
Security Awareness Training:
Regular and comprehensive security awareness training for all employees is crucial. Employees should be educated on recognizing and avoiding phishing scams, identifying malicious emails, and practicing safe browsing habits. Simulations and phishing tests can greatly improve employee awareness.
Regular Security Audits:
Regular security audits and penetration testing are essential for identifying vulnerabilities in the Office365 environment. This proactive approach allows companies to address security weaknesses before they can be exploited by attackers.
- Conduct regular vulnerability scans.
- Implement intrusion detection and prevention systems.
- Regularly update software and patches.
Conclusion:
This case demonstrates the devastating consequences of successful Office365 executive account hacks, resulting in significant financial losses and reputational damage. The methods used highlight the sophistication of modern cyberattacks. To prevent similar incidents, organizations must prioritize strengthening their Office365 security by implementing multi-factor authentication, providing comprehensive security awareness training, and conducting regular security audits. By taking proactive steps to secure your Microsoft Office 365 accounts and prevent Office365 executive account hacks, you can significantly reduce your vulnerability to these costly and damaging attacks. Don't wait until it's too late; prioritize your cybersecurity today.

Featured Posts
-
 A Mets Rivals Starting Pitcher A Breakthrough Season
Apr 28, 2025
A Mets Rivals Starting Pitcher A Breakthrough Season
Apr 28, 2025 -
 Predicting A Jarren Duran Esque Breakout This Red Sox Outfielder To Watch
Apr 28, 2025
Predicting A Jarren Duran Esque Breakout This Red Sox Outfielder To Watch
Apr 28, 2025 -
 Canadian Trade Mission To Southeast Asia Unlocking Energy Potential
Apr 28, 2025
Canadian Trade Mission To Southeast Asia Unlocking Energy Potential
Apr 28, 2025 -
 Open Ai Unveils Streamlined Voice Assistant Development Tools
Apr 28, 2025
Open Ai Unveils Streamlined Voice Assistant Development Tools
Apr 28, 2025 -
 Exploring The Florida Keys Overseas Highway From Railroad To Water
Apr 28, 2025
Exploring The Florida Keys Overseas Highway From Railroad To Water
Apr 28, 2025
