Investigation Uncovers Millions In Losses Due To Office365 Hacks

Table of Contents
The Rising Tide of Office365 Security Breaches
Office365, while offering numerous benefits, has become a prime target for sophisticated attacks. The increasing reliance on cloud services, coupled with the ever-evolving tactics of cybercriminals, makes organizations increasingly vulnerable to Office365 security breaches. Attackers exploit vulnerabilities in various Office365 applications and services, leveraging different attack vectors to gain unauthorized access.
- Increased reliance on cloud services: The shift towards cloud-based solutions, while beneficial, expands the attack surface for cybercriminals. More data resides in the cloud, making a successful breach potentially more damaging.
- Sophisticated attackers: Cybercriminals are constantly refining their techniques, developing more sophisticated methods to bypass security measures and compromise Office365 accounts.
- Lack of robust security measures: Many organizations fail to implement comprehensive security measures, leaving their Office365 environments vulnerable to exploitation. This often includes neglecting crucial aspects like multi-factor authentication and employee training.
- Attack Vectors: These attacks utilize various methods, including phishing emails designed to trick users into revealing credentials, credential stuffing using lists of stolen usernames and passwords, and malware infections that compromise endpoints and gain access to cloud resources.
Financial Ramifications of Office365 Compromises
The financial consequences of Office365 compromises can be crippling. Data breaches and ransomware attacks lead to significant direct and indirect costs. These costs extend far beyond the immediate financial loss, impacting an organization's reputation and long-term viability.
- Direct Financial Losses: Stolen funds, intellectual property theft, and the costs associated with data recovery represent substantial direct losses.
- Indirect Costs: Business disruption, lost productivity, and the time spent investigating and resolving the breach all contribute to significant indirect costs.
- Regulatory Fines and Legal Action: Non-compliance with data protection regulations (like GDPR or CCPA) can result in hefty fines and legal battles, further escalating financial losses.
- Reputational Damage: A data breach can severely damage an organization's reputation, leading to loss of customer trust and impacting future business opportunities. The cost of repairing a tarnished reputation can be immense.
Common Tactics Used in Office365 Hacks
Understanding the common tactics employed in Office365 hacks is crucial for effective prevention. Cybercriminals utilize a range of techniques, often combining several methods for maximum impact.
- Phishing Emails: These emails cleverly disguise themselves as legitimate communications from trusted sources, attempting to trick users into clicking malicious links or revealing their credentials. These emails often exploit current events or company-specific information to increase their effectiveness.
- Password Spraying: This technique involves systematically trying common passwords against multiple Office365 accounts, hoping to find weak or reused passwords.
- Malware Infections: Malware can infect endpoints (computers, laptops, mobile devices), gaining access to sensitive data and potentially spreading to the cloud environment through compromised accounts.
- Social Engineering: This involves manipulating employees through various psychological tactics to gain access to sensitive information or credentials. This can include pretexting, baiting, or quid pro quo.
- Exploiting Vulnerabilities: Attackers constantly scan for and exploit vulnerabilities in Office365 applications and services to gain unauthorized access. Keeping software patched and up-to-date is critical in mitigating this risk.
Best Practices for Preventing Office365 Hacks
Proactive security measures are essential to protect your organization from Office365 hacks. Implementing robust security practices is an investment that can save millions in potential losses.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain usernames and passwords.
- Security Awareness Training: Educating employees about phishing scams, social engineering tactics, and other threats is crucial. Regular training sessions significantly reduce the likelihood of successful phishing attacks.
- Software Updates: Regularly updating software with the latest security patches is paramount to closing vulnerabilities that attackers might exploit.
- Advanced Threat Protection: Utilize advanced threat protection tools that can detect and block malicious emails, malware, and other threats.
- Regular Access Reviews: Periodically review user access permissions to ensure that only authorized individuals have access to sensitive data. The principle of least privilege should be applied rigorously.
- Data Loss Prevention (DLP): Implement robust DLP measures to prevent sensitive data from leaving your organization's control, whether intentionally or unintentionally.
Safeguarding Your Business from Office365 Hacks
The investigation clearly demonstrates the significant financial losses associated with Office365 hacks. The cost of inaction far outweighs the investment in robust security measures. By implementing the best practices outlined above, organizations can significantly reduce their risk of becoming victims of Office365 breaches and protect their valuable data. Don't become another victim of Office365 hacks. Implement robust Office 365 security measures today to protect your valuable data and prevent devastating financial losses. Prioritize your Office 365 security and prevent costly Office365 breaches. Invest in comprehensive security solutions to mitigate risks associated with Office 365 security.

Featured Posts
-
 Nyt Mini Crossword Solution March 18 2024
May 20, 2025
Nyt Mini Crossword Solution March 18 2024
May 20, 2025 -
 How To Dress For Breezy And Mild Weather A Practical Guide
May 20, 2025
How To Dress For Breezy And Mild Weather A Practical Guide
May 20, 2025 -
 Pechalnaya Situatsiya Drug Raskryl Podrobnosti O Sostoyanii Shumakhera
May 20, 2025
Pechalnaya Situatsiya Drug Raskryl Podrobnosti O Sostoyanii Shumakhera
May 20, 2025 -
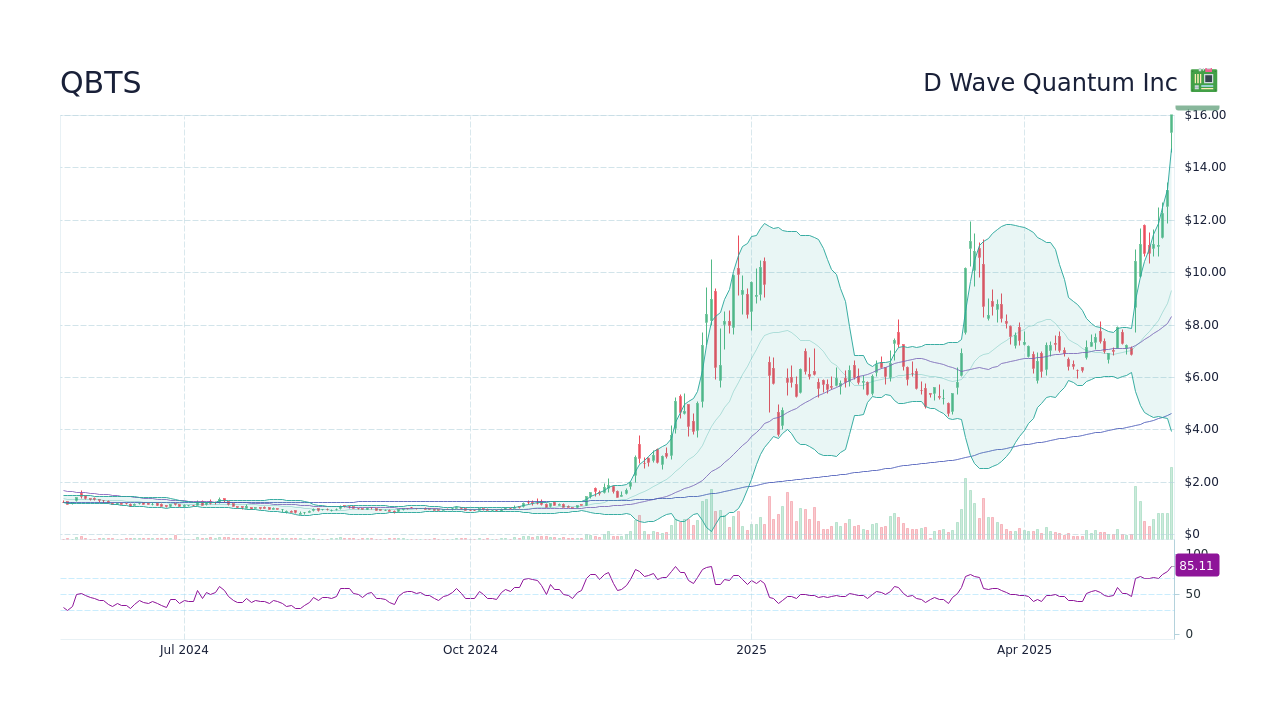 Analyzing The Recent Increase In D Wave Quantum Inc Qbts Stock
May 20, 2025
Analyzing The Recent Increase In D Wave Quantum Inc Qbts Stock
May 20, 2025 -
 Solve The Nyt Mini Crossword Answers And Hints For April 20 2025
May 20, 2025
Solve The Nyt Mini Crossword Answers And Hints For April 20 2025
May 20, 2025
