Millions In Losses After Office365 Executive Email Hack
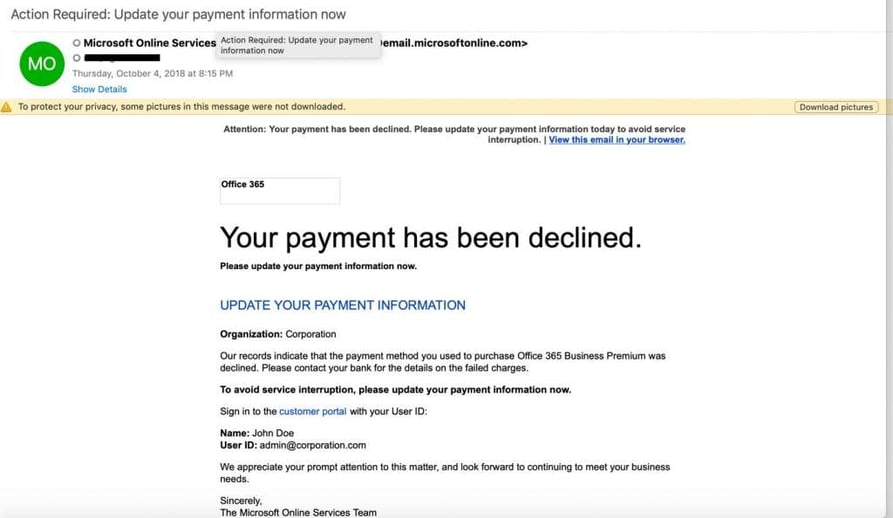
Table of Contents
The Scale of the Office365 Executive Email Hack and its Financial Impact
The financial impact of compromised executive email accounts can be devastating. While specific details about many incidents are kept confidential for legal and competitive reasons, reports indicate that losses from successful Office365 security breaches often reach millions of dollars. These breaches represent a significant threat to businesses of all sizes.
Financial Losses Detailed
One recent, publicly reported case involved a company losing over $2 million due to an Office365 executive email hack. The attackers used fraudulent wire transfers, impersonating the CEO to initiate payments to overseas accounts. This is a classic example of a Business Email Compromise (BEC) attack.
- Losses in this case totaled over $2 million.
- Funds were lost through fraudulent wire transfers initiated via compromised email.
- The attackers successfully impersonated a high-ranking executive.
This incident, and many others like it, highlights the urgent need for improved Office365 security and robust cybersecurity measures. The devastating financial losses associated with these BEC attacks involving Office365 are a wake-up call for organizations of all sizes.
Vulnerabilities Exploited in the Office365 Executive Email Hack
This particular Office365 executive email hack, and many others, exploited vulnerabilities stemming from a combination of technical weaknesses and human error.
Phishing and Social Engineering
The primary attack vector was a sophisticated spear-phishing campaign. The attackers crafted incredibly realistic emails designed to appear legitimate, targeting the executive's account specifically. These emails often contained malicious links or attachments, leading to malware installation or credential theft. Social engineering tactics were employed to manipulate the victim into divulging sensitive information or taking actions that compromised the account security.
- Spear-phishing emails, tailored to the executive's role and responsibilities, were used.
- Social engineering techniques built trust and persuaded the victim to take action.
- The attackers possibly exploited weak or default passwords, or used credential stuffing techniques.
The success of these attacks emphasizes the critical role of robust security awareness training in preventing Office365 vulnerabilities from being exploited.
Best Practices to Prevent Office365 Executive Email Hacks
Preventing Office365 executive email hacks requires a multi-layered approach combining technical safeguards with robust employee training.
Implementing Robust Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a critical first line of defense. MFA requires users to provide multiple forms of authentication to access their accounts, even if their password is compromised.
- MFA adds an extra layer of security, requiring something you know (password), something you have (phone, security key), or something you are (biometrics).
- Microsoft Authenticator app, hardware security keys, and other MFA methods offer strong protection.
- Enforcing MFA for all users, especially executives, significantly reduces the risk of unauthorized access.
Regular Security Awareness Training
Regular security awareness training is crucial to educating employees about phishing attacks and social engineering techniques.
- Regular training sessions should cover identifying phishing emails, recognizing social engineering tactics, and understanding the importance of secure password management.
- Simulated phishing campaigns can help assess employee vulnerability and reinforce training.
- Tailor training to the specific roles and responsibilities of your employees.
Advanced Threat Protection and Email Security Solutions
Investing in advanced email security solutions provides an additional layer of protection against sophisticated threats.
- Microsoft Defender for Office 365 offers advanced threat protection, including anti-phishing, anti-malware, and email authentication features.
- Consider third-party email security solutions that offer advanced features such as sandboxing and machine learning-based threat detection.
- Regular updates and patches are vital to keep your security software current and effective.
Conclusion
The recent Office365 executive email hack highlighting millions in financial losses underscores the critical need for robust cybersecurity measures. Exploiting vulnerabilities in phishing and social engineering, these attacks highlight the importance of proactive security strategies. Implementing multi-factor authentication, regular security awareness training, and advanced threat protection is not just advisable—it's essential. Protect your business from an Office365 executive email hack today! Learn more about securing your Office365 environment and preventing devastating financial losses.

Featured Posts
-
 Actors And Writers Strike A Complete Shutdown Of Hollywood
May 22, 2025
Actors And Writers Strike A Complete Shutdown Of Hollywood
May 22, 2025 -
 Unian Linsi Grem Zaklikaye Do Vidnovlennya Viyskovoyi Dopomogi Ukrayini
May 22, 2025
Unian Linsi Grem Zaklikaye Do Vidnovlennya Viyskovoyi Dopomogi Ukrayini
May 22, 2025 -
 Everything We Know About Netflixs Sirens Limited Series
May 22, 2025
Everything We Know About Netflixs Sirens Limited Series
May 22, 2025 -
 Increased Resistance To Ev Mandates From Car Dealers
May 22, 2025
Increased Resistance To Ev Mandates From Car Dealers
May 22, 2025 -
 Appeal Pending Ex Tory Councillors Wife Faces Decision On Racial Hatred Tweet
May 22, 2025
Appeal Pending Ex Tory Councillors Wife Faces Decision On Racial Hatred Tweet
May 22, 2025
