Office 365 Hacker's Multi-Million Dollar Scheme Exposed

Table of Contents
The Hacker's Modus Operandi: Exploiting Office 365 Vulnerabilities
The success of this multi-million dollar Office 365 hack hinges on the exploitation of several key vulnerabilities. The attackers cleverly combined various techniques to bypass security measures and gain access to sensitive data and financial resources.
Phishing and Social Engineering Attacks:
The initial phase of the attack relied heavily on phishing and social engineering. Hackers sent out meticulously crafted phishing emails designed to trick unsuspecting users into revealing their Office 365 credentials.
- Spoofed Email Addresses: Emails appeared to originate from legitimate sources, such as internal colleagues or trusted organizations.
- Urgent Requests: Emails often created a sense of urgency, pressuring recipients to click malicious links or download attachments without hesitation.
- Malicious Links: These links redirected users to fake login pages that mimicked the official Office 365 portal, designed to capture usernames and passwords.
- Compromised Credentials: Once obtained, these credentials provided the hackers with an easy entry point into victim accounts.
Credential Stuffing and Brute-Force Attacks:
Beyond phishing, the hackers employed credential stuffing—using stolen credentials from previous data breaches to access Office 365 accounts—and brute-force attacks—trying numerous password combinations until a successful match was found.
- Stolen Credentials: Data breaches on other platforms often expose usernames and passwords that are reused across multiple services, providing easy access to Office 365 accounts.
- Brute-Force Attacks: For accounts with stronger, unique passwords, the hackers employed automated brute-force attacks, utilizing sophisticated software to try numerous password combinations until they gained access.
- Exploited Vulnerabilities: While Microsoft regularly patches vulnerabilities, older, unpatched systems or misconfigurations within Office 365 environments could have been exploited.
Exploiting Weak Passwords and Multi-Factor Authentication Bypass:
A significant contributing factor to the success of this attack was the prevalence of weak passwords and the lack of robust multi-factor authentication (MFA) implementation.
- Weak Passwords: Many users employed easily guessable passwords, making them vulnerable to brute-force attacks and credential stuffing.
- MFA Bypass: While MFA significantly enhances security, some victims may not have had it enabled, or the hackers may have found ways to circumvent existing MFA measures.
- Data Breach Accessibility: Weak passwords obtained from other data breaches made it easier for the hackers to gain unauthorized access.
The Financial Impact of the Office 365 Hack: A Multi-Million Dollar Loss
The financial consequences of this Office 365 breach are staggering, with losses estimated in the millions of dollars.
Financial Losses Suffered by Victims:
- Theft of Funds: Hackers directly accessed and transferred funds from compromised accounts, leading to significant financial losses for individuals and businesses.
- Intellectual Property Theft: Confidential data, including sensitive business documents, intellectual property, and customer information, was stolen, causing irreparable damage to many organizations.
- Reputational Damage: The breach severely damaged the reputations of affected organizations, leading to loss of trust and potential legal action.
The Ripple Effect on the Economy:
The broader economic consequences of this Office 365 hack are significant.
- Remediation Costs: Victims incurred substantial costs associated with remediation, including forensic investigations, system recovery, and legal fees.
- Loss of Productivity: Disruptions to business operations due to the breach resulted in significant losses in productivity.
- Legal Ramifications: Potential legal battles and regulatory penalties add to the overall financial burden on affected organizations.
Lessons Learned and Enhanced Office 365 Security Practices
This devastating Office 365 security breach serves as a stark reminder of the importance of proactive security measures. To prevent similar incidents, organizations must implement robust security practices.
Strengthening Password Security and Implementing MFA:
- Password Managers: Encourage the use of reputable password managers to generate and store strong, unique passwords for all accounts.
- Strong Passwords: Enforce the use of complex passwords, combining uppercase and lowercase letters, numbers, and symbols.
- Regular Password Changes: Implement mandatory password rotation policies, requiring regular password changes.
- Multi-Factor Authentication (MFA): Mandate MFA for all Office 365 accounts, using methods like authenticator apps, security keys, or one-time codes.
Improving Phishing Awareness and Employee Training:
- Security Awareness Training: Regularly conduct comprehensive security awareness training programs for all employees, educating them about phishing scams, social engineering tactics, and safe online practices.
- Email Authentication: Utilize email authentication protocols (SPF, DKIM, DMARC) to prevent spoofed emails from reaching employees' inboxes.
- Phishing Simulations: Conduct regular phishing simulations to test employee awareness and identify vulnerabilities.
Regular Security Audits and Vulnerability Management:
- Regular Security Audits: Perform periodic security audits and penetration testing to identify and address vulnerabilities in the Office 365 environment.
- Vulnerability Management: Implement a robust vulnerability management program to promptly patch security flaws and address software updates.
- Threat Intelligence Feeds: Leverage threat intelligence feeds to stay ahead of emerging threats and proactively mitigate potential risks.
Conclusion: Protecting Your Organization from Office 365 Hacks
This multi-million dollar Office 365 hacking scheme underscores the critical need for enhanced security measures. The attackers effectively exploited vulnerabilities related to weak passwords, a lack of MFA, and susceptibility to phishing attacks. The financial losses, both direct and indirect, were substantial. To protect your organization, prioritize robust password policies, mandatory MFA, regular security awareness training, and ongoing vulnerability management. Don't become the next victim. Strengthen your Office 365 security today by implementing robust password policies, enabling multi-factor authentication, and providing regular security awareness training to your employees. Learn more about protecting your organization from similar Office 365 attacks and secure your future.

Featured Posts
-
 Turning Trash To Treasure An Ai Powered Poop Podcast From Mundane Documents
Apr 24, 2025
Turning Trash To Treasure An Ai Powered Poop Podcast From Mundane Documents
Apr 24, 2025 -
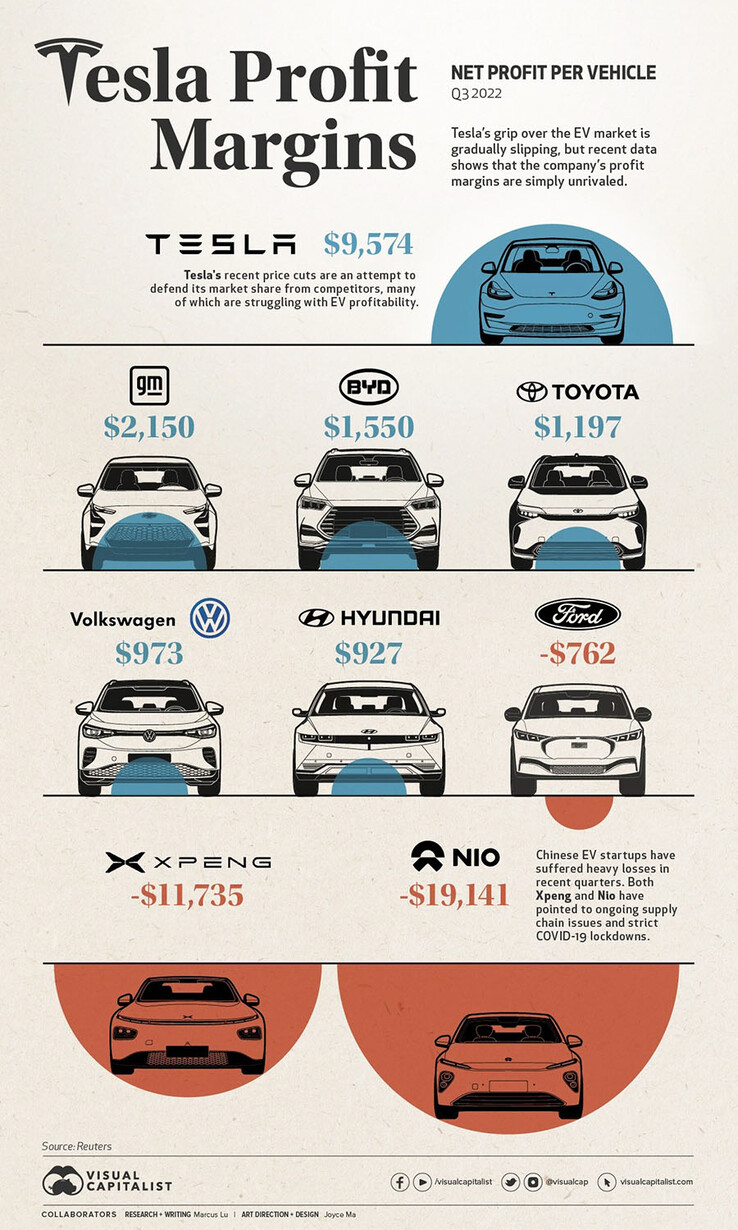 Teslas Falling Profits Analyzing The Influence Of Musks Political Ties
Apr 24, 2025
Teslas Falling Profits Analyzing The Influence Of Musks Political Ties
Apr 24, 2025 -
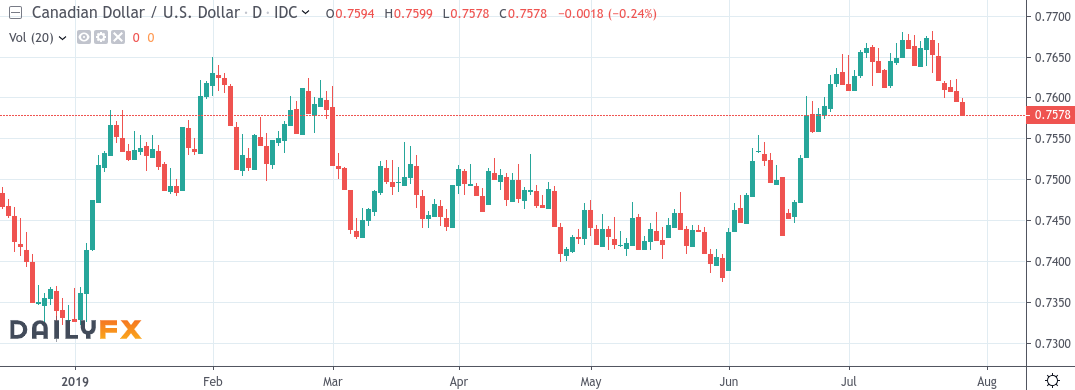 Understanding The Recent Fluctuations In The Canadian Dollar
Apr 24, 2025
Understanding The Recent Fluctuations In The Canadian Dollar
Apr 24, 2025 -
 Oblivion Remastered Now Available From Bethesda
Apr 24, 2025
Oblivion Remastered Now Available From Bethesda
Apr 24, 2025 -
 Are Trumps Budget Cuts Fueling A More Dangerous Tornado Season
Apr 24, 2025
Are Trumps Budget Cuts Fueling A More Dangerous Tornado Season
Apr 24, 2025
