Office365 Executive Inboxes Targeted: Millions Stolen, FBI Claims
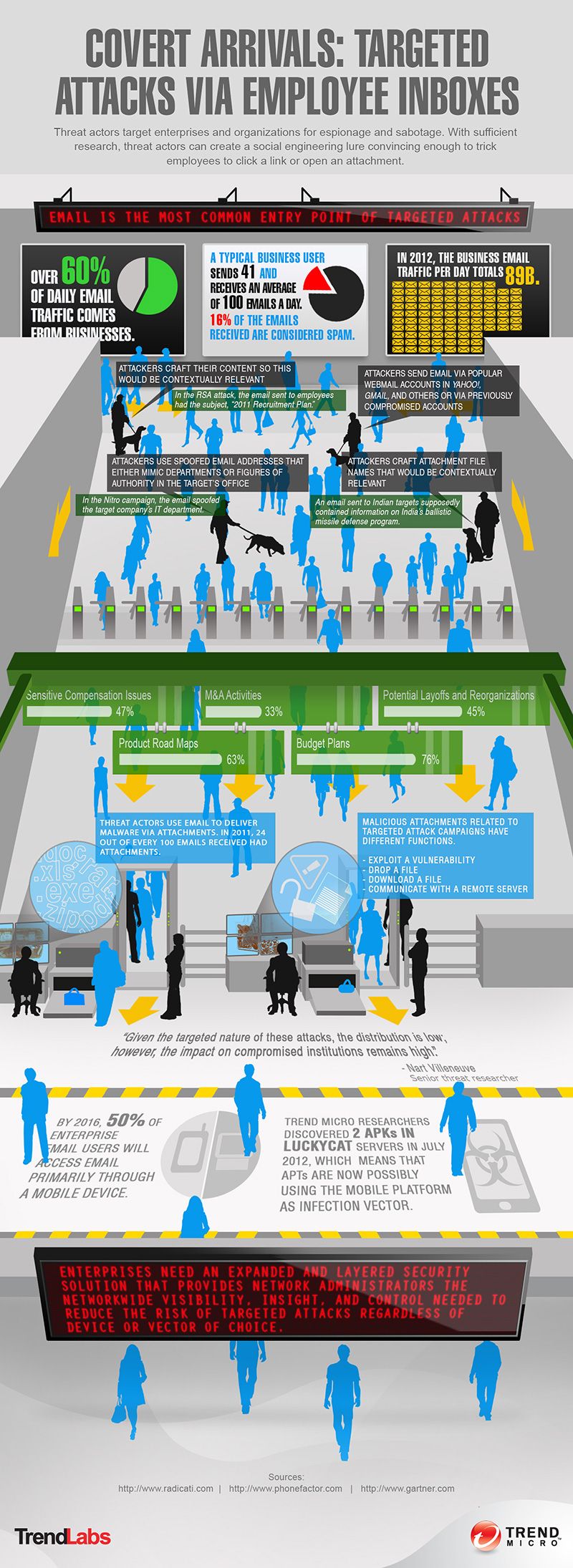
Table of Contents
The Scale of the Office365 Executive Inbox Compromise
The FBI's report on the financial losses stemming from compromised Office365 executive accounts paints a concerning picture. Millions of dollars have vanished, highlighting the devastating financial impact of these targeted attacks. The sheer scale of the problem is likely underestimated, as many organizations are hesitant to publicly report security breaches due to reputational concerns. This reluctance to disclose incidents makes accurate assessment of the overall impact difficult but underscores the serious nature of the threat.
- Financial Losses: The reported millions in losses represent a significant financial burden for affected organizations. These losses extend beyond the stolen funds, encompassing the costs of investigation, remediation, and legal fees.
- Underreported Incidents: The true number of successful Office365 security breaches is likely significantly higher than reported figures, indicating a widespread vulnerability. Many smaller organizations may lack the resources to fully investigate and report such incidents.
- Vulnerability of Office365: The reliance on Office365 for sensitive financial transactions and internal communications makes it a prime target for cybercriminals. The convenience and accessibility of the platform are attractive features but also present considerable risks if not properly secured.
- Rising Costs of Data Breaches: The average cost of a data breach continues to rise exponentially, impacting profitability and long-term sustainability for businesses. This includes not only financial losses but also damage to brand reputation and customer trust.
Methods Used in Targeting Office365 Executive Inboxes
Cybercriminals employ increasingly sophisticated techniques to target Office365 executive inboxes. These attacks often combine multiple methods to maximize their chances of success. The goal is to gain unauthorized access to sensitive data, including financial information and intellectual property.
- Spear Phishing: Attackers utilize highly targeted spear phishing campaigns, crafting emails that appear to originate from trusted sources. These emails are personalized to appear legitimate, making them more likely to be opened and clicked.
- Malware and Ransomware: Once access is gained, malicious software, including ransomware, is often deployed to encrypt data and demand a ransom for its release. This can cripple an organization's operations and lead to further financial losses.
- Credential Harvesting: Deceptive websites or malicious attachments are used in credential harvesting attacks, aiming to steal usernames and passwords. These credentials are then used to gain access to accounts and systems.
- Exploiting Vulnerabilities: Cybercriminals actively seek and exploit known Office365 vulnerabilities to gain unauthorized access. Regular software updates and patching are crucial to mitigate this risk.
- Social Engineering: Social engineering tactics, such as pretexting and baiting, are used to manipulate employees into revealing sensitive information or clicking malicious links. Human error remains a significant vulnerability in any organization's cybersecurity defenses.
Understanding the Phishing Techniques Employed
The sophistication of phishing techniques used in these attacks is alarming. Cybercriminals use increasingly refined methods to bypass security measures.
- Email Spoofing: Attackers skillfully spoof legitimate email addresses, making their phishing emails appear authentic and trustworthy. This makes it incredibly difficult for recipients to distinguish between legitimate and fraudulent emails.
- Malicious Links: Emails often contain malicious links that redirect users to websites designed to steal credentials or install malware. These websites often mimic legitimate login pages to trick users.
- Compromised Accounts: Once an executive's account is compromised, attackers can use it to launch further attacks within the organization, gaining access to additional data and systems. This is often known as lateral movement.
- Advanced Persistent Threats (APTs): In some cases, these attacks represent Advanced Persistent Threats (APTs), involving long-term, sophisticated attacks designed to infiltrate organizations and remain undetected for extended periods.
Protecting Your Organization from Office365 Executive Inbox Attacks
Protecting against these sophisticated attacks requires a multi-layered approach encompassing technology, training, and policy. Organizations must prioritize robust security measures to safeguard their data and systems.
- Multi-Factor Authentication (MFA): Implementing MFA for all Office365 accounts, especially executive inboxes, is paramount. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access, even if they obtain credentials.
- Security Awareness Training: Regular and comprehensive security awareness training is crucial to educate employees about phishing and social engineering tactics. Employees must be able to recognize and report suspicious emails and attachments.
- Email Security Solutions: Investing in robust email security solutions, including advanced threat protection and anti-spam filters, can significantly reduce the risk of malicious emails reaching inboxes.
- Threat Intelligence: Leverage threat intelligence feeds to stay ahead of emerging threats and proactively identify and address potential vulnerabilities. This provides early warning signs of emerging attack vectors.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan to minimize the impact of a successful attack. A well-defined plan ensures a swift and effective response to security breaches.
- Software Updates: Regularly update software and operating systems to patch known security vulnerabilities. Keeping systems updated is essential to close security gaps that attackers could exploit.
Conclusion
The FBI's warning about the millions of dollars stolen through compromised Office365 executive inboxes serves as a stark reminder of the ever-evolving cybersecurity landscape. Organizations must prioritize robust email security, implement multi-factor authentication, and invest in comprehensive security awareness training to mitigate the risks. Failure to adequately protect Office365 executive inboxes leaves organizations vulnerable to significant financial losses, reputational damage, and operational disruption. Don't wait for a devastating attack; take proactive steps to strengthen your Office365 security and protect your organization from this escalating threat. Secure your Office365 executive inboxes today.

Featured Posts
-
 Geopolitika S Sh A Protiv Evropy Sravnenie Strategiy
May 04, 2025
Geopolitika S Sh A Protiv Evropy Sravnenie Strategiy
May 04, 2025 -
 The Rising Costs Of Offshore Wind Power A Shifting Investment Landscape
May 04, 2025
The Rising Costs Of Offshore Wind Power A Shifting Investment Landscape
May 04, 2025 -
 Fox 2 To Simulcast Select Red Wings And Tigers Games
May 04, 2025
Fox 2 To Simulcast Select Red Wings And Tigers Games
May 04, 2025 -
 Former Ufc Champions May 3rd Fight A Year In The Making
May 04, 2025
Former Ufc Champions May 3rd Fight A Year In The Making
May 04, 2025 -
 The Count Of Monte Cristo A Modern Look At A Classic Swashbuckler
May 04, 2025
The Count Of Monte Cristo A Modern Look At A Classic Swashbuckler
May 04, 2025
