Office365 Security Breach: Millions Lost, Executive Inboxes Targeted
Table of Contents
The Rising Tide of Office365 Breaches
The frequency of successful Office365 security breaches is alarming. Attackers are employing increasingly sophisticated techniques to gain unauthorized access and exploit vulnerabilities within the platform. This section explores the primary attack vectors.
Phishing and Spear Phishing Attacks
Phishing and spear phishing emails remain the most common entry point for Office365 breaches. These cleverly crafted emails often mimic legitimate communications, aiming to trick users into revealing credentials or downloading malware. Executive email compromise (EEC) is a particularly damaging form of spear phishing, targeting high-level employees with access to sensitive financial and strategic information.
- Examples of phishing techniques: Spoofed email addresses, urgent requests for immediate action, links to malicious websites, attachments containing malware.
- Successful attack vectors: Exploiting vulnerabilities in email clients, bypassing multi-factor authentication (MFA) through social engineering, leveraging compromised accounts.
- Social engineering tactics: Creating a sense of urgency, using authority figures or trusted brands to build credibility, leveraging personal information to personalize attacks.
Statistics show a shocking success rate for phishing attacks. According to [insert reputable source and statistic here], a significant percentage of Office365 users fall victim to phishing attempts annually. This highlights the critical need for robust employee training and security awareness programs.
Exploiting Vulbilities in Office365 Applications
Malicious actors aren't just targeting email; they're also exploiting vulnerabilities within various Office365 applications like SharePoint, Teams, and OneDrive. These applications often store sensitive data, making them prime targets for attackers.
- Examples of vulnerabilities: Unpatched software, weak access controls, insecure configurations, outdated plugins.
- How they are exploited: By leveraging known vulnerabilities (CVEs), using brute-force attacks to gain access, exploiting zero-day exploits before patches are available.
- Patch management importance: Regular updates and patching are crucial to mitigating the risk of exploitation.
Zero-day exploits represent a significant threat, as they target vulnerabilities unknown to the software vendor. These attacks require a proactive and layered security approach, including intrusion detection and prevention systems.
Compromised Third-Party Applications
Many organizations integrate third-party applications with Office365 to enhance productivity and functionality. However, these apps can introduce significant security risks if not properly vetted and managed.
- Examples of risky apps: Unverified apps from unknown developers, apps with inadequate security measures, apps with excessive permissions.
- Importance of app vetting: Thoroughly research and vet all third-party applications before integration. Check reviews, security certifications, and developer reputation.
- Best practices for third-party app management: Regularly review app permissions, enforce strong password policies, and monitor app usage for suspicious activity.
Compromised third-party apps can provide attackers with backdoor access to your entire Office365 environment, potentially leading to widespread data breaches and ransomware attacks.
The Devastating Consequences of an Office365 Breach
The consequences of a successful Office365 security breach can be far-reaching and devastating, impacting your bottom line, reputation, and customer trust.
Financial Losses
The financial impact of a data breach can be significant, encompassing a wide range of expenses.
- Examples of high-profile breaches and their financial costs: [Insert examples and associated costs].
- Potential for ransomware attacks and associated costs: Ransomware attacks can cripple operations, leading to significant downtime costs, ransom payments, and data recovery expenses.
Legal fees, regulatory fines (GDPR, CCPA, etc.), and the cost of incident response and remediation can quickly add up, totaling millions of dollars in some cases.
Data Loss and Intellectual Property Theft
Losing sensitive data, such as customer information, intellectual property, trade secrets, and strategic plans, can have long-term consequences.
- Types of sensitive data at risk: Customer Personally Identifiable Information (PII), financial data, employee data, intellectual property, confidential business plans.
- Long-term impact of data breaches on customer trust: Breaches can severely damage customer trust, leading to loss of business and reputational harm.
Non-compliance with data protection regulations can result in substantial fines and legal action.
Reputational Damage
A security breach can severely damage your brand reputation and customer loyalty.
- Examples of companies that suffered reputational damage due to breaches: [Insert examples].
- Importance of proactive communication and crisis management: Having a well-defined incident response plan and communicating transparently with stakeholders is crucial for mitigating reputational damage.
The negative publicity surrounding a breach can impact investor confidence and make it difficult to attract new customers.
Strengthening Your Office365 Security Posture
Proactive measures are essential to protect your organization from Office365 security breaches.
Implementing Multi-Factor Authentication (MFA)
MFA is a critical first line of defense against phishing and other credential-theft attacks.
- Different MFA methods: SMS codes, authenticator apps, security keys, hardware tokens.
- Benefits of MFA: Significantly reduces the risk of unauthorized access even if credentials are compromised.
- Easy implementation steps: Most Office365 plans offer easy-to-implement MFA features.
MFA adds an extra layer of security, making it exponentially harder for attackers to gain access even if they obtain your username and password.
Regular Security Awareness Training
Educating your employees about phishing and other social engineering tactics is crucial.
- Best practices for security awareness training: Regular training sessions, interactive simulations, phishing campaigns, clear guidelines on handling suspicious emails.
- Frequency of training: Regular refresher training is essential to maintain awareness.
- Engaging training methods: Use a variety of engaging methods to keep employees interested and involved.
Training employees to identify and report suspicious emails and attachments is paramount to prevent successful phishing attacks.
Utilizing Advanced Security Features in Office365
Leverage Office365's built-in security features to enhance your protection.
- Key features of ATP and Defender: Advanced threat detection, anti-malware, anti-phishing, URL filtering, sandboxing.
- Benefits of using these tools: Proactive threat detection and prevention, real-time protection against malware and phishing attacks.
Microsoft Defender for Office 365 and Advanced Threat Protection (ATP) offer advanced capabilities to protect your organization from sophisticated threats.
Regular Security Audits and Penetration Testing
Proactive security assessments are vital to identify and address vulnerabilities.
- Types of security audits: Vulnerability scans, security configuration reviews, compliance audits.
- Benefits of penetration testing: Simulates real-world attacks to identify weaknesses in your security posture.
- Frequency of assessments: Regular audits and penetration tests should be conducted at least annually, or more frequently depending on your risk profile.
Regular security audits and penetration testing help identify weaknesses in your security posture before they can be exploited by attackers.
Conclusion
Office365 security breaches are a significant and growing threat to businesses of all sizes. The financial and reputational consequences can be devastating. By understanding the common attack vectors, implementing robust security measures, and proactively addressing vulnerabilities, organizations can significantly reduce their risk of falling victim to an Office365 security breach. Don't wait until it's too late – take action today to strengthen your Office365 security posture and protect your valuable data and reputation. Invest in comprehensive Office365 security solutions and training to safeguard your business from the ever-evolving threats in the digital landscape. Implement strong Office 365 security practices to prevent costly and reputation-damaging breaches.

Featured Posts
-
 Town Women Aim For Top Spot Gwalia Match Preview
May 12, 2025
Town Women Aim For Top Spot Gwalia Match Preview
May 12, 2025 -
 Shevchenko Vs Fiorot Champions Dismissive Remarks Fuel Ufc Rivalry
May 12, 2025
Shevchenko Vs Fiorot Champions Dismissive Remarks Fuel Ufc Rivalry
May 12, 2025 -
 34 Cars Set For Indy 500 As Satos Entry Confirmed
May 12, 2025
34 Cars Set For Indy 500 As Satos Entry Confirmed
May 12, 2025 -
 Reyting Zelenskogo Dzhonson Oprovergaet Zayavlenie Trampa O 4
May 12, 2025
Reyting Zelenskogo Dzhonson Oprovergaet Zayavlenie Trampa O 4
May 12, 2025 -
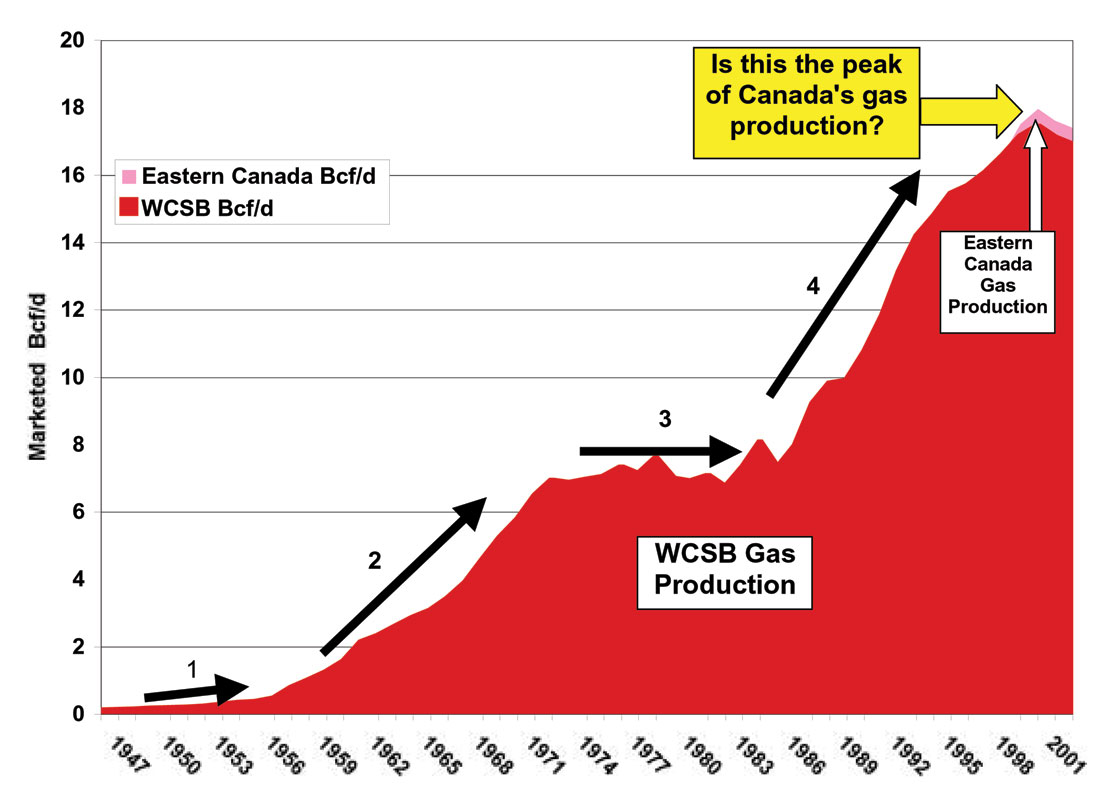 Analyzing The Expansion Of Canadas Top Natural Gas Producer
May 12, 2025
Analyzing The Expansion Of Canadas Top Natural Gas Producer
May 12, 2025
