Block Mirror: Circumventing Censorship And Accessing Blocked Content
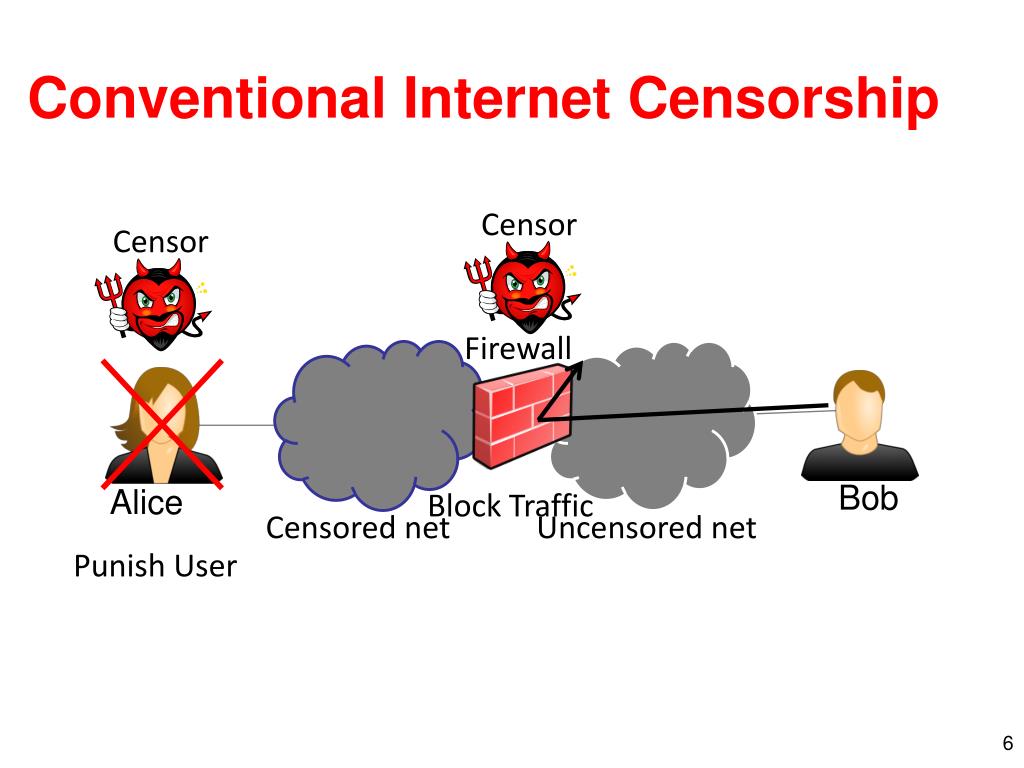
Table of Contents
Understanding Block Mirrors and How They Work
A block mirror is essentially a replicated version of a website or online resource, hosted on a server outside the jurisdiction imposing the censorship. This means it's a copy of the original website, but located in a place where access isn't restricted. They bypass censorship by providing an alternative access point, circumventing geographical restrictions and firewalls that block the original site.
There are several types of block mirrors:
-
Dedicated mirrors: These are official copies of a website, created and maintained by the website owners themselves to provide redundancy or access in restricted areas.
-
Unofficial mirrors: These are created by third parties and may not always be up-to-date or reliable. They often arise in response to censorship or high traffic demands on the original site.
-
Archive sites: Websites like the Wayback Machine archive versions of websites over time. While not strictly "block mirrors," they can provide access to content that's no longer available on the live site, including content that may have been censored.
-
Key characteristics of Block Mirrors:
- Mirrors replicate the original website's content, structure, and functionality as accurately as possible.
- They often utilize different domain names or IP addresses to evade blocks imposed by firewalls or government censorship.
- Finding reliable block mirrors requires caution and due diligence, as many unofficial mirrors may be unreliable or even malicious.
Benefits of Using Block Mirrors to Access Blocked Content
Block mirrors offer several significant advantages:
-
Access to restricted information: Gain access to news, social media platforms, educational resources, and other content blocked in your region due to censorship or geographical restrictions. This is particularly valuable for staying informed and accessing a wide range of perspectives.
-
Circumventing censorship: Overcome government restrictions and firewalls that limit access to information. This is crucial for maintaining online freedom and accessing uncensored news and viewpoints.
-
Freedom of information: Access diverse perspectives and viewpoints that may be suppressed in your region. This allows for a broader understanding of global events and issues.
-
Key advantages summarized:
- Enhances online freedom and access to information, promoting a more informed citizenry.
- Can be crucial for journalists, researchers, activists, and anyone seeking unrestricted access to information.
- Allows users to bypass geographical limitations for streaming services, accessing content not available in their region.
Risks Associated with Using Block Mirrors
While block mirrors offer significant benefits, it's crucial to be aware of the potential risks:
-
Security risks: Unofficial mirrors may contain malware, phishing attempts, or other malicious code designed to steal your data or compromise your system. Always exercise caution.
-
Legal implications: Accessing blocked content may have legal consequences in some jurisdictions. It's essential to understand the laws in your region regarding access to restricted online materials.
-
Data privacy concerns: Unsecured mirrors could compromise your personal information if they lack proper encryption (HTTPS).
-
Mitigating the risks:
- Always verify the legitimacy of a block mirror before accessing it. Look for reputable sources or reviews.
- Use a VPN (Virtual Private Network) for added security and privacy. A VPN encrypts your internet traffic and masks your IP address.
- Be aware of local laws and regulations regarding access to blocked content. Ignorance of the law is not a defense.
Identifying and Evaluating Reliable Block Mirrors
Identifying trustworthy block mirrors requires careful evaluation:
-
Trusted Sources: Look for mirrors linked from trusted and reputable news sources, organizations, or individuals known for their commitment to accurate information.
-
SSL Certificates (HTTPS): Ensure the mirror uses HTTPS to encrypt your connection and protect your data from interception. Look for the padlock icon in your browser's address bar.
-
Consistency Check: Compare the content and design of the mirror to the original website. Significant discrepancies could indicate a fraudulent or unreliable mirror.
-
Red Flags to Watch Out For:
- Avoid mirrors with suspicious URLs or poorly designed interfaces. Legitimate mirrors usually maintain a similar look and feel to the original site.
- Read user reviews and feedback before using an unfamiliar mirror. Check online forums or review sites for comments from other users.
- Cross-reference information found on a mirror with other reliable sources to verify its accuracy.
Best Practices for Safe and Effective Use of Block Mirrors
To maximize the benefits and minimize the risks of using block mirrors:
-
Use a VPN: A VPN enhances your online anonymity and security by encrypting your internet traffic and masking your IP address, making it harder for malicious actors to track your activity.
-
Antivirus/Anti-malware Software: Employ robust antivirus and anti-malware software to protect your system from potential threats. Keep your software updated.
-
Caution with Links/Downloads: Be extremely cautious about clicking links or downloading files from unofficial block mirrors. Malware is often disguised as legitimate content.
-
Essential Security Habits:
- Regularly update your security software to benefit from the latest threat protection.
- Be aware of phishing attempts and malware threats. Legitimate websites will never ask for your passwords or other sensitive information via email or unsolicited messages.
- Exercise caution when entering personal information on a mirror site. Only use mirrors from trusted sources that employ robust security measures.
Conclusion
Block Mirrors provide a valuable tool for circumventing censorship and accessing blocked content. However, it's crucial to understand the associated risks and employ best practices to ensure your online security and privacy. By carefully evaluating mirrors, using a VPN, and practicing safe browsing habits, you can effectively utilize block mirrors to access information freely while mitigating potential threats. Remember to always prioritize online safety when exploring the world of block mirrors and accessing restricted content. Learn more about maximizing your online freedom and choosing the most reliable block mirror solutions.

Featured Posts
-
 San Jose Earthquakes Vs Opponent A Quakes Epicenter Preview
May 15, 2025
San Jose Earthquakes Vs Opponent A Quakes Epicenter Preview
May 15, 2025 -
 Choosing The Right Black Decker Steam Iron Features And Comparisons
May 15, 2025
Choosing The Right Black Decker Steam Iron Features And Comparisons
May 15, 2025 -
 Padres Sweep Giants In Petco Park Showdown
May 15, 2025
Padres Sweep Giants In Petco Park Showdown
May 15, 2025 -
 Is Dustin Poirier Retiring Paddy Pimblett Wants A Piece Of The Action
May 15, 2025
Is Dustin Poirier Retiring Paddy Pimblett Wants A Piece Of The Action
May 15, 2025 -
 What Is Creatine And Should You Take It A Complete Guide
May 15, 2025
What Is Creatine And Should You Take It A Complete Guide
May 15, 2025
