Cybercriminal Made Millions Targeting Executive Office365 Accounts
Table of Contents
The Modus Operandi: How the Cybercriminal Targeted Executive Accounts
The cybercriminal employed a multi-pronged approach, leveraging a combination of sophisticated techniques to target executive Office365 accounts. This wasn't a simple brute-force attack; it involved highly targeted spear phishing campaigns and exploitation of known vulnerabilities. The methods employed included:
-
Highly personalized phishing emails designed to bypass spam filters: These emails weren't generic spam; they were meticulously crafted, containing insider information and personalized details to increase the chances of the recipient falling victim. The social engineering involved was exceptionally advanced, often impersonating trusted colleagues or clients to gain the target's confidence.
-
Exploiting known vulnerabilities in Office365 to gain unauthorized access: The cybercriminal likely identified and exploited known vulnerabilities in Office365's systems or leveraged zero-day exploits to gain initial access. This highlights the critical need for organizations to stay up-to-date with security patches and updates.
-
Use of credential stuffing and brute-force attacks against weaker passwords: For accounts with weaker passwords, the cybercriminal may have employed credential stuffing – using lists of stolen usernames and passwords from other data breaches – or brute-force attacks, attempting numerous password combinations until a successful match was found. This underscores the importance of strong, unique passwords for each account.
-
Leveraging compromised accounts to launch further attacks, potentially ransomware or data exfiltration: Once access was gained, the cybercriminal likely used the compromised accounts to launch further attacks, potentially deploying ransomware to encrypt sensitive data and demand a ransom payment, or exfiltrating valuable data for resale on the dark web. This highlights the potential for cascading damage from a single compromised account.
The Devastating Impact: Financial and Reputational Losses
The consequences of successful attacks against executive Office365 accounts can be catastrophic, resulting in significant financial and reputational damage. The millions amassed by this single cybercriminal represent just a fraction of the total global losses from similar attacks. The impact includes:
-
Direct financial losses from ransomware payments or fraudulent transactions: Ransomware attacks can cripple an organization, demanding significant payments to regain access to critical data. Furthermore, compromised accounts can be used for fraudulent transactions, leading to substantial financial losses. In this case, the cybercriminal made millions through a combination of these methods.
-
The significant cost of incident response and remediation efforts: Responding to a data breach involves extensive investigation, remediation, and legal consultation, all of which incur substantial costs. This can easily run into hundreds of thousands or even millions of dollars.
-
Reputational damage and loss of customer trust following a data breach: A data breach severely impacts an organization's reputation, eroding customer trust and potentially leading to loss of business. The negative publicity surrounding such an incident can have long-term consequences.
-
Potential regulatory fines and legal liabilities: Depending on the nature of the data breached and the applicable regulations (like GDPR or CCPA), organizations face significant regulatory fines and legal liabilities. These penalties can easily outweigh the financial losses from the initial attack itself.
Protecting Your Organization: Strengthening Office365 Security
Protecting your organization from these sophisticated attacks requires a multi-layered approach to security. Implementing robust security measures is paramount to mitigate the risk. Key strategies include:
-
Mandatory multi-factor authentication (MFA) for all users, especially executives: MFA adds an extra layer of security, requiring users to verify their identity through a second factor, such as a code from a mobile app or a security key. This significantly reduces the risk of unauthorized access even if credentials are compromised.
-
Comprehensive security awareness training for employees to recognize phishing attempts: Regular security awareness training helps employees identify and report phishing emails and other social engineering tactics. This training should include realistic examples and simulations.
-
Implementing advanced threat protection solutions to detect and block malicious emails and attachments: Advanced threat protection solutions utilize AI and machine learning to detect and block sophisticated threats that may bypass traditional email security filters.
-
Utilizing data loss prevention (DLP) tools to prevent sensitive data from leaving the organization: DLP tools monitor data movement and prevent sensitive data from being exfiltrated from the organization's network.
-
Enforcing strong password policies and using a password manager: Strong, unique passwords are essential, and a password manager can help employees manage these passwords securely.
-
Regular security audits and penetration testing to identify vulnerabilities: Regular security audits and penetration testing help identify and address vulnerabilities before they can be exploited by cybercriminals.
The Role of AI and Machine Learning in Cybersecurity
AI and machine learning are playing an increasingly vital role in enhancing cybersecurity defenses. These technologies can help organizations detect anomalies, predict potential threats, and automate responses to security incidents more effectively. Anomaly detection systems, powered by AI, can identify unusual patterns in network traffic or user behavior that might indicate a cyberattack. Machine learning algorithms are also crucial in identifying and classifying malware and phishing attempts.
Conclusion
The case of the cybercriminal targeting executive Office365 accounts serves as a stark reminder of the ever-evolving and increasingly sophisticated threat landscape. The financial and reputational consequences of successful attacks can be devastating, impacting not only the bottom line but also long-term business sustainability. Organizations must prioritize robust cybersecurity measures, including multi-layered security solutions and comprehensive employee training programs, to protect themselves from this growing threat.
Don't become the next victim. Invest in comprehensive Office365 security solutions and employee training to safeguard your organization from costly and damaging cyberattacks targeting executive accounts. Learn more about protecting your business from this threat today.

Featured Posts
-
 Monstrous Beauty A Feminist Reimagining Of Chinoiserie At The Met
Apr 28, 2025
Monstrous Beauty A Feminist Reimagining Of Chinoiserie At The Met
Apr 28, 2025 -
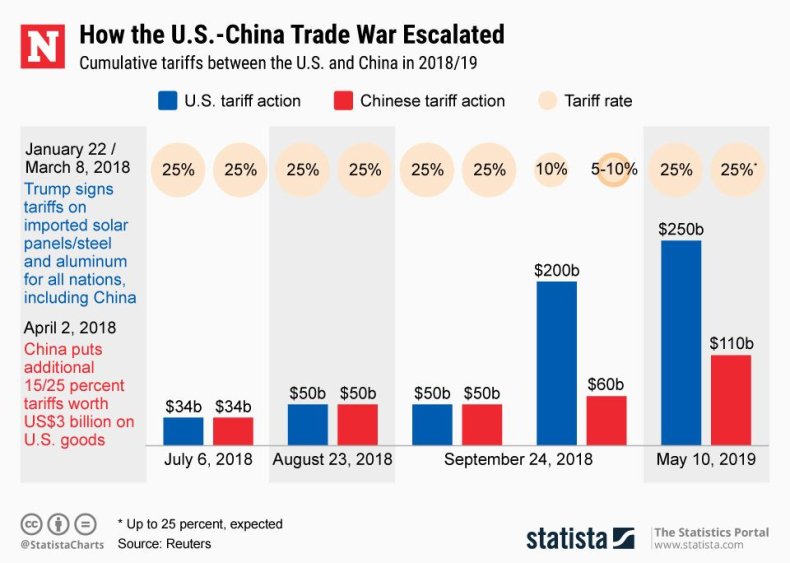 Us China Trade Some Products Escape Tariffs
Apr 28, 2025
Us China Trade Some Products Escape Tariffs
Apr 28, 2025 -
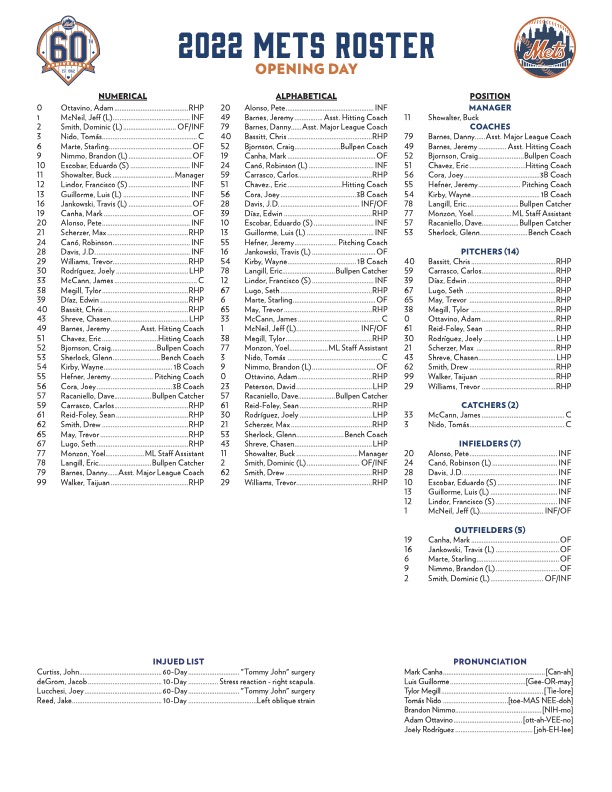 Predicting The Mets Opening Day Roster A Spring Training Week 1 Analysis
Apr 28, 2025
Predicting The Mets Opening Day Roster A Spring Training Week 1 Analysis
Apr 28, 2025 -
 Hudsons Bay Liquidation Shop Now For Huge Savings
Apr 28, 2025
Hudsons Bay Liquidation Shop Now For Huge Savings
Apr 28, 2025 -
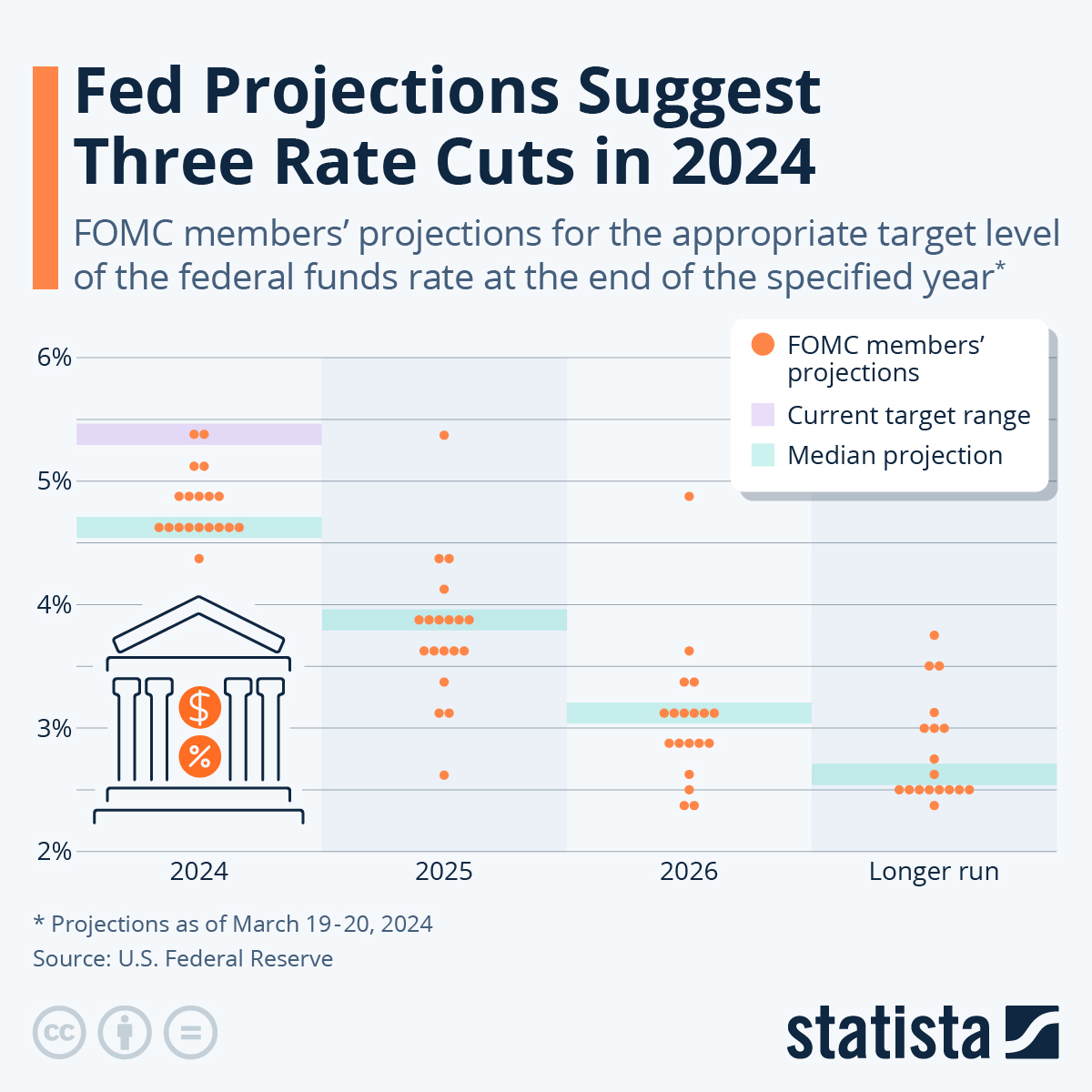 Grim Retail Sales A Sign Of Rate Cuts To Come
Apr 28, 2025
Grim Retail Sales A Sign Of Rate Cuts To Come
Apr 28, 2025
