Federal Charges: Hacker Made Millions From Executive Office365 Accounts

Table of Contents
The Hacker's Modus Operandi: Exploiting Office 365 Vulnerabilities
This highly organized cybercrime operation leveraged a multi-pronged approach to breach executive Office 365 accounts. The hacker didn't rely on a single vulnerability but instead employed a combination of techniques to maximize their chances of success.
Phishing and Social Engineering
The hacker likely used sophisticated phishing emails and social engineering techniques to gain initial access. These attacks preyed on human vulnerabilities, exploiting trust within organizations to gain access to sensitive information.
- Examples of Phishing Techniques: Highly personalized emails mimicking legitimate communications from trusted sources (e.g., internal IT, executives, or financial institutions). These emails often contained malicious links or attachments designed to install malware or harvest credentials.
- Targeting Specific Individuals: The hacker likely researched their targets, identifying key executives with access to financial systems and sensitive data. This targeted approach increased the likelihood of a successful phishing campaign.
- Exploiting Trust Within Organizations: The attacker may have used internal organizational knowledge gleaned from publicly available information or previous smaller breaches to make the phishing emails more convincing.
- Malware and Tools: The hacker may have employed various malware tools, including keyloggers to capture passwords, and remote access Trojans (RATs) to maintain persistent access to compromised systems.
Credential Stuffing and Brute-Force Attacks
In addition to phishing, the hacker might have employed credential stuffing – using stolen credentials from other breaches to attempt access to Office 365 accounts. If those failed, brute-force attacks, where the attacker systematically tries various password combinations, may have been used.
- Password Managers and Multi-Factor Authentication (MFA): The use of strong, unique passwords, coupled with password managers and MFA, are crucial in mitigating these attacks. MFA adds an extra layer of security, requiring more than just a password to access an account, significantly reducing the effectiveness of both credential stuffing and brute-force attacks.
- Importance of Strong, Unique Passwords: Using strong, unique passwords for each account is paramount. Weak or reused passwords represent a significant vulnerability that hackers actively exploit.
Exploiting Weak Security Configurations
The success of the attack may have also hinged on exploiting weaknesses in the targeted organizations' Office 365 security configurations. Many organizations fail to implement best practices, leaving their systems vulnerable.
- Examples of Weak Security Configurations: Lack of multi-factor authentication (MFA), insufficient access controls (allowing excessive permissions to less privileged users), and failure to regularly update software and security patches.
- Microsoft Security Best Practices: Microsoft provides extensive documentation and resources on securing Office 365. Following these best practices, including regularly reviewing user permissions and enabling advanced security features, is vital in preventing such breaches.
The Financial Ramifications: Millions Lost Through Wire Fraud and Other Schemes
The hacker allegedly used compromised executive Office 365 accounts to perpetrate sophisticated financial crimes.
Wire Fraud and Account Takeover
Once inside, the hacker could initiate fraudulent wire transfers, manipulating payment systems and diverting funds to their own accounts. This involved taking over the email accounts of executives involved in financial transactions.
- Specific Examples of Fraudulent Activities: The indictment likely details specific examples of fraudulent wire transfers, invoice manipulation, and other schemes used to siphon money from the victim organizations.
- Scale of Financial Losses: The millions of dollars stolen highlight the significant financial impact of such attacks, impacting not only the financial stability of affected organizations, but also the livelihoods of their employees and investors.
- Impact on Victimized Organizations: Beyond the financial losses, these attacks can cause significant reputational damage, impacting investor confidence and customer relationships.
Data Exfiltration and Extortion
Beyond financial theft, the hacker may have also engaged in data exfiltration, stealing sensitive information and potentially selling it on the dark web or using it for extortion purposes.
- Consequences of Data Breaches: Data breaches can lead to significant legal liabilities, regulatory fines (like GDPR penalties), and reputational damage, impacting an organization's long-term viability.
The Legal Response: Federal Charges and the Ongoing Investigation
The legal response to this cybercrime underscores the seriousness of the offenses and the growing focus on prosecuting cybercriminals.
The Charges Filed
The specific federal charges filed against the hacker likely include wire fraud, computer fraud, and identity theft.
- Potential Penalties: The potential penalties are severe, including lengthy prison sentences, substantial fines, and restitution to the victims.
The Investigation and its Implications
The ongoing investigation has implications for future cybersecurity efforts, highlighting the need for collaboration between law enforcement and the private sector.
- Combating Cybercrime: Law enforcement agencies are increasingly collaborating to combat cybercrime, sharing intelligence and resources to track down perpetrators and disrupt their operations.
- Incident Response Planning: The incident highlights the critical importance of having a robust incident response plan. Organizations need to be prepared to identify, contain, and recover from cyberattacks effectively.
- Cybersecurity Awareness: The case underscores the need for improved cybersecurity awareness training for employees. Educating employees about phishing scams, social engineering tactics, and safe password practices is vital in preventing future attacks.
Conclusion
This case of federal charges against a hacker who made millions targeting executive Office 365 accounts underscores the critical need for robust cybersecurity measures. The sophistication of the attacks highlights the vulnerability of even the most secure systems to determined and resourceful cybercriminals. The financial losses and potential reputational damage emphasize the importance of proactive measures.
Call to Action: Protect your organization from similar Office 365 hacks. Implement strong password policies, multi-factor authentication, regular security audits, and employee cybersecurity training. Learn more about securing your Office 365 environment and preventing costly data breaches. Don't become the next victim of a devastating Office 365 attack.

Featured Posts
-
 V Mware Costs To Skyrocket At And T Reports 1050 Price Hike From Broadcom
May 10, 2025
V Mware Costs To Skyrocket At And T Reports 1050 Price Hike From Broadcom
May 10, 2025 -
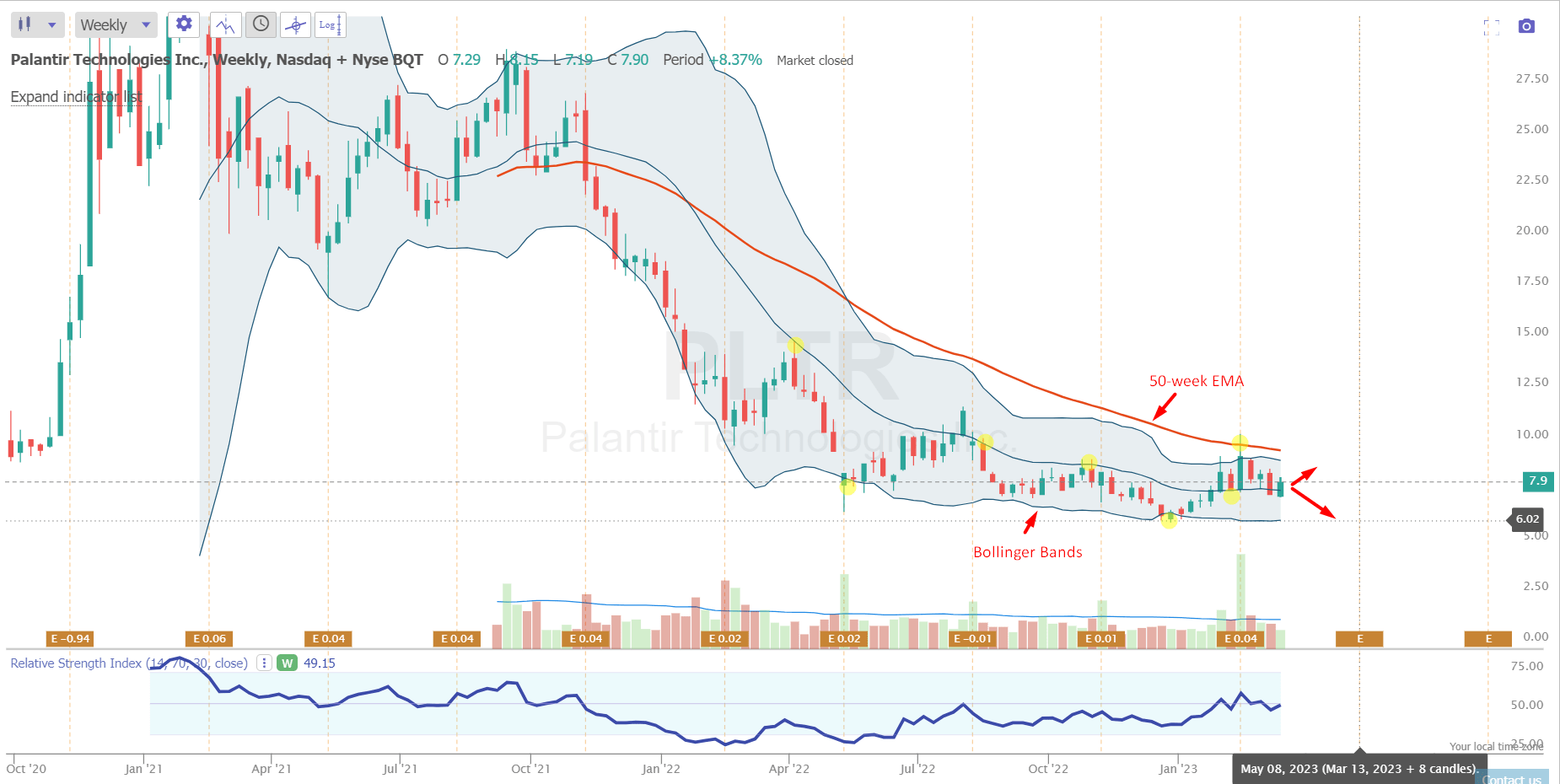 Palantir Stock Decline A Detailed Analysis And Investment Recommendation
May 10, 2025
Palantir Stock Decline A Detailed Analysis And Investment Recommendation
May 10, 2025 -
 Sharing Your Story How Trumps Executive Orders Affected Transgender People
May 10, 2025
Sharing Your Story How Trumps Executive Orders Affected Transgender People
May 10, 2025 -
 London Outing Harry Styles Debuts A 70s Style Mustache
May 10, 2025
London Outing Harry Styles Debuts A 70s Style Mustache
May 10, 2025 -
 Mstwa Fyraty Me Alerby Bed Antqalh Mn Alahly Almsry
May 10, 2025
Mstwa Fyraty Me Alerby Bed Antqalh Mn Alahly Almsry
May 10, 2025
