T-Mobile's $16 Million Data Breach Fine: Three Years Of Security Failures
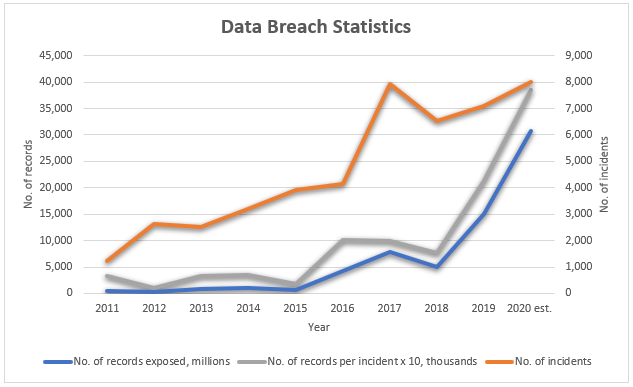
Table of Contents
The Extent of the Data Breach and its Impact
The T-Mobile data breach was far-reaching, impacting a substantial number of customers and exposing sensitive personal information. The scale of the breach and the types of data compromised underscore the severity of the security failures. The impact of this data breach extended far beyond a simple inconvenience; it posed significant risks to affected individuals.
- Number of affected customers: While the exact number fluctuates depending on the specific breach discussed, reports indicate potentially millions of T-Mobile customers were affected across multiple incidents.
- Types of data compromised: The compromised data included highly sensitive personal information such as names, addresses, Social Security numbers, driver's license information, and financial details. In some cases, even account PINs and other credentials were exposed.
- Potential risks to affected individuals: The exposure of this sensitive personal information created significant risks for affected individuals, including identity theft, credit card fraud, and financial losses. The potential for long-term financial and emotional distress is substantial.
- Examples of reported customer harm: Following the breach, numerous reports surfaced detailing the hardships faced by customers who experienced identity theft, fraudulent credit applications, and other financial repercussions.
Three Years of Security Neglect: Identifying Key Failures
The $16 million fine wasn't levied for a single lapse; rather, it reflects a pattern of security failures spanning three years. This prolonged period of vulnerability underscores the systemic nature of the problem and the lack of adequate preventative measures. T-Mobile's cybersecurity infrastructure was demonstrably deficient in several key areas.
- Specific vulnerabilities exploited: Investigations revealed vulnerabilities stemming from weak passwords, outdated software, and insufficient encryption protocols. These vulnerabilities allowed unauthorized access to sensitive customer data.
- Lack of multi-factor authentication: The absence of robust multi-factor authentication significantly weakened security, making it easier for attackers to bypass initial login protections.
- Insufficient monitoring and detection systems: Inadequate monitoring and detection systems failed to identify and respond to malicious activity in a timely manner, allowing the breach to persist for an extended period.
- Inadequate incident response plan: A poorly defined or inadequately tested incident response plan hampered T-Mobile's ability to contain the breach and mitigate its impact. Delays in reporting the breach further exacerbated the problem.
Regulatory Scrutiny and the $16 Million Fine
The Federal Trade Commission (FTC) launched an investigation into T-Mobile's security practices following the data breaches. The resulting $16 million fine reflects the severity of the violations and serves as a strong deterrent against future negligence.
- Specific regulations violated: The FTC cited violations of various data security and privacy regulations, highlighting the company's failure to implement reasonable security measures to protect customer data.
- Details of the FTC investigation: The investigation uncovered a series of security lapses, including the failure to implement basic security controls and inadequate responses to known vulnerabilities.
- Breakdown of the $16 million fine: The fine was levied to compensate for the costs associated with the breach, including customer notification, credit monitoring services, and other remediation efforts.
- Potential long-term effects on T-Mobile's business: Beyond the financial penalty, the breach has damaged T-Mobile's reputation, potentially impacting customer loyalty and future business prospects.
Lessons Learned and Best Practices for Mobile Security
The T-Mobile data breach offers crucial lessons for businesses across all sectors. Preventing future data breaches requires a multi-faceted approach focusing on proactive security measures and a robust security culture.
- Implement multi-factor authentication: Multi-factor authentication adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Regularly update software and security patches: Promptly applying software updates and security patches closes known vulnerabilities and reduces the risk of exploitation.
- Invest in intrusion detection and prevention systems: Sophisticated monitoring and detection systems can identify and respond to threats in real-time, minimizing the impact of potential breaches.
- Conduct regular security audits and penetration testing: Regular security assessments help identify vulnerabilities before they can be exploited by attackers.
- Develop and regularly test incident response plans: A well-defined and tested incident response plan is crucial for effectively managing a data breach and minimizing its impact.
- Train employees on cybersecurity best practices: Educating employees about cybersecurity risks and best practices helps create a security-conscious culture and reduces the likelihood of human error.
Conclusion
T-Mobile’s $16 million data breach fine serves as a stark reminder of the significant costs associated with neglecting data security. The three years of security failures leading to this penalty highlight the critical need for proactive and comprehensive security measures in the mobile industry and beyond. The scale of the T-Mobile data breach and the resulting fine should act as a catalyst for improved data protection strategies across the board.
Call to Action: Don't let your business become the next victim of a costly data breach. Invest in robust data security measures and learn from T-Mobile's experience to protect your customer data and your company's reputation. Prioritize mobile security and prevent costly T-Mobile-level data breaches. Proactive data security is not just good business practice; it's a necessity in today's digital landscape.

Featured Posts
-
 Trump Defends Obamacare At Supreme Court A Win Could Boost Rfk Jr S Influence
Apr 22, 2025
Trump Defends Obamacare At Supreme Court A Win Could Boost Rfk Jr S Influence
Apr 22, 2025 -
 Activision Blizzard Merger Faces Ftc Appeal
Apr 22, 2025
Activision Blizzard Merger Faces Ftc Appeal
Apr 22, 2025 -
 Turning Poop Into Podcast Gold How Ai Simplifies Scatological Document Analysis
Apr 22, 2025
Turning Poop Into Podcast Gold How Ai Simplifies Scatological Document Analysis
Apr 22, 2025 -
 The Countrys Emerging Business Hubs An Interactive Map
Apr 22, 2025
The Countrys Emerging Business Hubs An Interactive Map
Apr 22, 2025 -
 Antitrust Scrutiny Intensifies Could Google Be Broken Up
Apr 22, 2025
Antitrust Scrutiny Intensifies Could Google Be Broken Up
Apr 22, 2025
